The fourth iteration of cybersecurity challenge poses the ultimate test: who can hack a satellite in space?
Five teams in the annual Space Systems Command co-sponsored Hack-A-Sat cybersecurity competition this August (HAS4) will face the ultimate challenge: hack an active satellite in space.

Moonlighter, a 3U CubeSat satellite built by the Aerospace Corporation, will be launched this summer on a Space X Falcon 9 rocket as part of an International Space Station (ISS) resupply mission. Moonlighter, which weighs approximately 11 pounds and is almost 12 inches long, will be put into a Low Earth Orbit (LEO), awaiting the final HAS4 competition at DEF CON 31, August 11 to 13, in Las Vegas.
The winning team will receive a $50,000 prize and will also have bragging rights that are truly — out of this world.
“The Moonlighter satellite is absolutely a big highlight for all of us,” said Manfred Paul, a member of the Krautsat team that took first place during the qualifications competition.
“A major draw to the competition comes from the chance to interact with and learn about real-world space systems and software; it’s just not something people outside of that field get to ‘play around’ with very often.”
Wyatt Neal, one of the members of SpaceBitsRUs, the third-place qualifications finishing team, said, “To say the team is excited is an understatement! Everyone is really pumped just to see what’s going to happen; we know the competition is already designed to be challenging and space just makes everything harder.”
Hack-A-Sat is a Capture the Flag (CTF) competition that is designed to inspire the world’s top cybersecurity talent to develop the skills necessary to help reduce vulnerabilities and build more secure space systems, organizers said.
This is the fourth year for the competition, sponsored by the U.S. Department of the Air Force, Space Systems Command (SSC) and the Air Force Research Laboratory (AFRL).
“The cost/benefit for this competition is far better than what we’ve seen in the past,” said Capt. Kevin J. Bernert, SSC Hack-A-Sat Program Manager. “Traditionally, to put something on at this scale and get this much information out of it, would cost a lot more. We can actually observe these competitors using tactics, techniques and procedures that can help inform future space vehicle design to make them more secure. If there are any vulnerabilities that we spot, we can take that into consideration for future space systems.”
Another benefit of the competition is educating the cybersecurity community and the general public about the importance of space assets to the world’s economy and national security. Understanding what the vulnerabilities are, and the need to protect those assets, “especially as space is becoming easier to access,” Bernert said, adding, “The cost of launching is getting driven down, and a lot more of our infrastructure that people use every day revolves around assets that are in space. This is a win for everybody if people understand the importance of securing all those systems — not just the military, but commercial, as well.
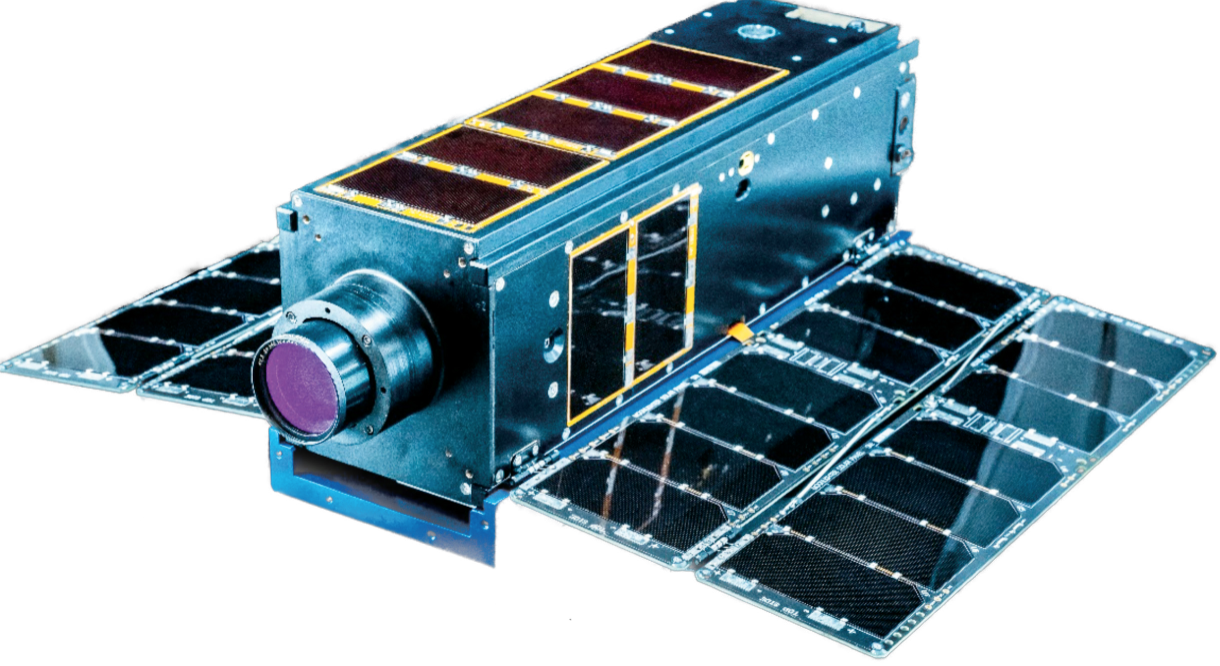
The Moonlighter satellite, courtesy of The Aerospace Corporation.
Bernert continued, “The space industry itself is growing rapidly because everything is becoming more reliant on space. We want to excite people and show them the tie-in between all the cyber-security principles that you’re practicing on the ground and how they can be applied to our space systems, too.”
“For us, the biggest thing we gain is the internal networking opportunities for the team and the chance to work and collaborate with people we wouldn’t normally get to interact with,” Wyatt Neal said. “The competition is so fast-paced and it allows the team to rapidly innovate on effective but imperfect solutions and then learn how to improve them collaboratively. This type of competition also gives us the chance to really challenge our members from all different skill sets to learn, teach and grow.”
“One goal the competition has definitely succeeded in is bringing people from cybersecurity and space- related fields together,” Manfred Paul added.
“We’ve made a lot of new contacts, and also had a lot of exchange of knowledge in both directions – many of those from the cybersecurity side probably didn’t know much about orbit calculations and attitude control systems a few years ago. Hack-A- Sat forces you to learn about those things, while still applying the ‘hacker mindset’ to them. Also, the contest makes it easy to rediscover that certain fascination of space. Personally, Hack-A-Sat sometimes makes me want to go outside, look up in the night sky and thing about how much more there is out there to explore — and hack!”
Hack-A-Sat Teams can range from one person to 100 people or more in number. This year, more than 725 teams comprised of 2,700+ individuals from all over the world competed in the qualification rounds that were conducted from April 1-2. The top five teams are:
• Krautsat, a 75-member team made up of mostly German CTF teams and people with backgrounds in space science
• mhackeroni, an Italian team that had its best finish
• SpaceBitsRUs, a team made up of about 120 Northrop Grumman employees from across the company, which won second place and $30,000 in last year’s HAS3
• Poland Can Into Space, the $50,000 first-place winner of last year’s HAS3
• jmp fs: [rcx]
Many are repeat participants in the annual challenge. For example, a team named Solar Wine placed 3rd and won a $20,000 prize last year and the year before, that team was the first place winner.
Poland Can Into Space took second place in 2021 and DiceGang came in third. In 2020, the Poland
Can Into Space and FluxRepeatRocket were among the top three winners and now, three years later, several members of FluxRepeatRocket are part of team Krautsat.
During the April 2023 qualification rounds, teams logged in to quals.2023.hackasat.com and completed a number of challenges over a two-day period, said Mark Werremeyer, senior software engineer with Cromulence, the cybersecurity company that designed and hosted the HAS competition.

On the website, competitors could see a scoreboard which listed the challenges with links to access them, and occasionally, files to help them accomplish the task, Werremeyer said. These challenges required skills in in RISC-V ROP chaining, heap exploitation, satellite communications, phased array antennas, maneuvering into Mars orbit, cracking crypto, speculative execution, and space math.
Some challenges were asynchronous in nature, similar to satellite operations where commands must be scheduled and the resulting telemetry is available only at a future contact.
If completed correctly, the system rewarded the team with a “flag” — a long sequence of random characters tied to that team, which they then submitted to score points.
Wyatt Neal described this year’s qualification rounds as “Intense! I think the hosts aimed to bring the different engineering disciplines together. Some of the challenges could not be solved by a single skill set – you had to blend several disciplines together. A really great example of that was getting our reverse engineers talking with the orbital teams over a ranging filter challenge.”
Despite the competition name, hacking isn’t the only skill required. Successful teams need to have people who understand orbital mechanics, radio frequency (RF) communications, satellite operations, astrophysics, and reverse engineering, as well as the ability to exploit development and vulnerability research, Capt. Bernert said, adding, “The teams that really fare the best are the ones that have members all of those areas. Some people can be experts on radio frequency communications or orbital mechanics, but if they don’t have the knack for reverse engineering or exploit development, they’ll be able to solve some challenges but not all of them.”
Just as space operations is a 24/7 field, the competition ran from 10:00 a.m. on a Saturday to 4:00 p.m. on the following day, requiring teams to work in shifts and manage their sleep, Werremeyer said. “Depending on which challenges are coming up, they try and make sure their crypto expert or their space math expert will get some sleep when those challenges aren’t active and then come back to solve them when those challenges do unlock.
“For HAS2, we had a flat sat built for each team and they would have to control that satellite and solve challenges on it. But it was a flat sat, sitting on, basically, a desk with the other flat sats. Last year, for HAS3, we did full digital twins and emulated the satellite’s hardware — that hardware was running the flight software we built for those spacecraft. Each team had their own digital twin spacecraft in a simulated space physics environment and they could command it, attack other satellites and defend their own satellites.
“This year, the big difference is we’re launching the Moonlighter spacecraft, so we’ll have one actual, physical spacecraft that will be part of the game and teams will have to solve challenges on that,” Werremeyer noted.
While competitors will be able to access Moonlighter, the satellite has a “sandbox” portion for the competition, and other controls that the HAS team can use to make sure its batteries are still charged and communications run smoothly, said Aaron Myrick, project leader at The Aerospace Corporation, the only federally funded research and development center for the entire space enterprise.

The satellite has no propulsion unit on board — hackers won’t be able to send the smallsat careening out of its orbit or into another satellite, Myrick said.
Moonlighter is comprised of a camera that will use the stars to calculate a vehicle orientation; a payload camera; a set of circuit boards that include a power routing board, attitude control board and the command and data handling computer, a GPS antenna to receive signals for position and time; a radio antenna to send telemetry and receive commands from ground operators; a payload radio to send telemetry and receive commands from ground operators over a high-speed link; a gyro to measure the rate and acceleration of the satellite’s rotation in multiple directions; X-Axis, Y-Axis and Z-Axis reaction wheels, to adjust the pointing of the satellite along the X, Y and Z axis when the wheel speed or direction changes; and a sun sensor to measure the light received to aid in determining the direction of the sun.
“This satellite is unique because we have built it from the ground up to be a cyber-experimentation test bed,” Myrick said. “In a lot of satellite designs, we have a payload for a mission — whether that’s imaging or communication — but in this case, what we’re trying to do is test out different cyber technologies using a space platform. We had to design almost the entire vehicle and ground segment in a different way than would normally have been completed.
“It was almost a little bit backwards as we’re trying to think of the ways we want the vehicle to go into a type of failure conditions, different ways to attack the vehicle and then be able to recover from those,” Myrick added, noting that Aerospace began designing the satellite in 2021. “That was very important in the concept design: making sure everything is recoverable, and sometimes from different pathways."
“For me, it was an interesting progression in my career because we’ve done some cyber exercises in the past and used end-of-life or residual ops satellites,” Myrick said. “In those exercises, we couldn’t really do a lot with the vehicle as they just weren’t designed for cyber exercises. As we’re designing Moonlighter from the ground up, we’re able to do all of the things we’ve wanted to do. It’s one thing to do these things on a digital twin and flat sats, but when you’re doing things on-orbit and it’s real, that just brings it to an entirely different level. There’s going to be lessons learned out of this for all who are involved in this exercise. I’m excited to get this opportunity to do this — there’s no bigger stage than this for a hacker competition.”
In the past, space was a much more benign environment and the United States could orbit satellites without worrying about any threats, other than natural phenomena.
“A lot of the space-grade hardware was honestly boutique and hard to acquire,” Myrick said. “However, today, many of the Low Earth orbit constellations use automotive or industrial grade components because they survive just fine in LEO and that’s driven down the cost and also their availability; however, at the same time, this has driven the need to have more cyber-resilient systems.”
Aerospace will continue to operate Moonlighter after the competition, Myrick said, noting, “Eventually, the vehicle will acquire enough atmospheric drag that it will burn up in the atmosphere — we estimate its lifetime at about a year and a half. We are talking with various government organizations within the U.S. Space Force to become involved in activities beyond Hack-A-Sat.”
How will organizers manage to top HAS4 next year?
 Subject matter experts contributing to this article: From left to right: Mark Werremeyer, senior software engineer with Cromulence Aaron Myrick, project leader at The Aerospace Corporation Capt. Kevin Bernert, SSC Hack-A-Sat Program Manager
Subject matter experts contributing to this article: From left to right: Mark Werremeyer, senior software engineer with Cromulence Aaron Myrick, project leader at The Aerospace Corporation Capt. Kevin Bernert, SSC Hack-A-Sat Program Manager
Bernert said the details are still being worked out and the team will also be taking feedback from HAS4 participants into account. He said, “People tell us, ‘This stuff is really, really hard,’ which is good. It’s not meant to be easy, because space is hard.”
Learn more about the competition at hackasat.com and follow along on Twitter @hack_a_sat.
Space Systems Command is the U.S. Space Force Field Command responsible for acquiring and delivering resilient war fighting capabilities to protect our nation’s strategic advantage in and from space. The Command manages an $15 billion space acquisition budget for the Department of Defense and works in partnership with joint forces, industry, government agencies, academic and allied organizations to accelerate innovation and outpace emerging threats. Our actions today are making the world a better space for tomorrow.
Contact Space Systems Command at SSC@spaceforce.mil — also, follow on LinkedIn


