
Cloud computing is one of the fundamental technologies that has been, and continues to be, a large factor in the evolution of our modern world, and it is defined as the delivery of computing services — including servers, storage, databases, networking, software, analytics, and intelligence — over the Internet (“the cloud”).
While many organizations have migrated away from physical computing infrastructure to the cloud, the idea of migrating to a cloud-based system is still met with apprehension from some organizations — especially organizations in highly-regulated industries such as aerospace and defense.

The reason for apprehension is the perception that cloud-based systems are inherently less secure than physical, on-premise systems. However, many organizations that rely on secure data for their existence are proving this notion is outdated and incorrect. Image for post Image for post Cloud Computing by ProSymbols from the Noun Project Cloud computing services, such as Amazon Web Services (AWS) and Microsoft Azure, are being used to overhaul and modernize the IT operations of U.S. defense and intelligence agencies. In 2013, a $600 million secure cloud was developed by Amazon Web Services for the Central Intelligence Agency (CIA), and it now services all 17 intelligence agencies.
An example of a contract granted by the DoD to a cloud computing service provider is the recent $10 billion JEDI contract given to Microsoft in order to modernize its infrastructure so DoD personnel can access and manipulate data, regardless of location. The DoD also plans to use this cloud technology to support ongoing innovations in artificial intelligence.
The Pentagon may be one of the most secure areas on the planet, both in a physical and cyber sense, and now has invested $10 billion to move from an antiquated technological infrastructure to a nimble, equally or potentially more secure, cloud-based one.
A recent New York Times article stated, “Federal officials have said government won’t fully maximize the benefits of the cloud until it focuses more on the opportunities it can provide than worrying about cybersecurity, and indeed many agencies with particularly sensitive information have begun to overcome these fears.”
The National Security Agency (NSA) is also moving all its mission data to a classified cloud environment. Commercial cloud services are also used by blue chip corporations such as Apple (Apple iCloud), GE
Oil & Gas, Samsung, and Netflix to scale operations, to become more nimble, to drive costs down, and to realize greater growth and profitability — all while maintaining extremely high levels of cybersecurity. Netflix may not have been the streaming superpower as we know it, had the company not overhauled their technology and migrated fully to the cloud.
These organizations, and the industries they are in, have continued to evolve with greater computing power through cloud technology. Our mission ground control technology, Major Tom, works in tandem with AWS and Azure to offer the same potential to organizations who use satellites in space to conduct missions.
As previously mentioned, AWS is the same cloud technology used by the CIA, and through AWS or Azure, Major Tom is compliant with the rigorous cybersecurity measures dictated by the National Institute of Standards and Technology (NIST) 800–53 Revision 4 framework. Furthermore, Major Tom will be eligible for FedRAMP compliance — a federal government-focused compliance with even more stringent guidelines than those given by NIST.
Major Tom’s cybersecurity strength not only lies in its ability to protect data from hackers and other bad actors, but also in the fact that it guarantees an enterprise’s data is stored and hosted on a geographically isolated US, EU, Asia, South America or other national server and not elsewhere (i.e. not hosted in a country in which the primary user country does not have amicable relations with). Also, it ensures that only specified entities can access the enterprise’s data in the cloud. This type of compliance is known as Government Cloud compliance (GovCloud).
Kubos, as a founding member of the Orbital Security Alliance, understands the paramount importance of cybersecurity. It is also apparent that the U.S. military and intelligence agencies also understand that cybersecurity in space is of utmost importance to any organization or country that is developing a footprint in space through space-related missions. In fact, the United States Air Force, alongside the Defense Digital Service, held a Space Security Challenge at DefCon 2020 (one of the world’s longest running and largest hacking conventions): Hack-a-Sat.
This is a challenge that brought the world’s best security researchers and hackers from all organizations and agencies to solve cybersecurity challenges on space systems, and ultimately attempt to hack a satellite. The idea is this: the Pentagon is investing heavily in space-based programs, with a focus on building out satellite networks, and if the Pentagon increases its satellite presence in space, it must also deeply understand cybersecurity to protect those satellites. Back to Kubos security standards: Major Tom enforces server-side HTTPS for all user interaction as well as all ground station and scripting interfaces.
HTTPS is a secure web protocol that protects data from unauthorized viewing, tampering, or misuse. This protocol makes sure users are safe from advanced spoofing, injection, and man-in-the-middle attacks. For Major Tom Enterprise, encryption certificates — certificates containing keys used to encrypt electronic messages, files, documents, or data transmissions — are renewed yearly through Amazon and/or Microsoft as the root certificate issuer. For Major Tom On-Premise (“air-gap”) licenses, the certificate issuer and renewal process is fully configurable by the customer. All certificates use SHA-256 with RSA Encryption. In short, Kubos upholds the highest levels of security measures.
Kubernetes was developed and designed by engineers at Google as an open source container orchestration platform that automates manual processes involved in deploying, managing, and scaling containerized applications. Through Kubernetes, Major Tom can enforce fine-grained access control through both Ingress and Firewall configuration.
According to RedHat Inc., one of the first companies to work with Google on Kubernetes, “Kubernetes clusters can span hosts across on-premise, public, private, or hybrid clouds. For this reason, Kubernetes is an ideal platform for hosting cloud-native applications that require rapid scaling, like real-time data streaming.”
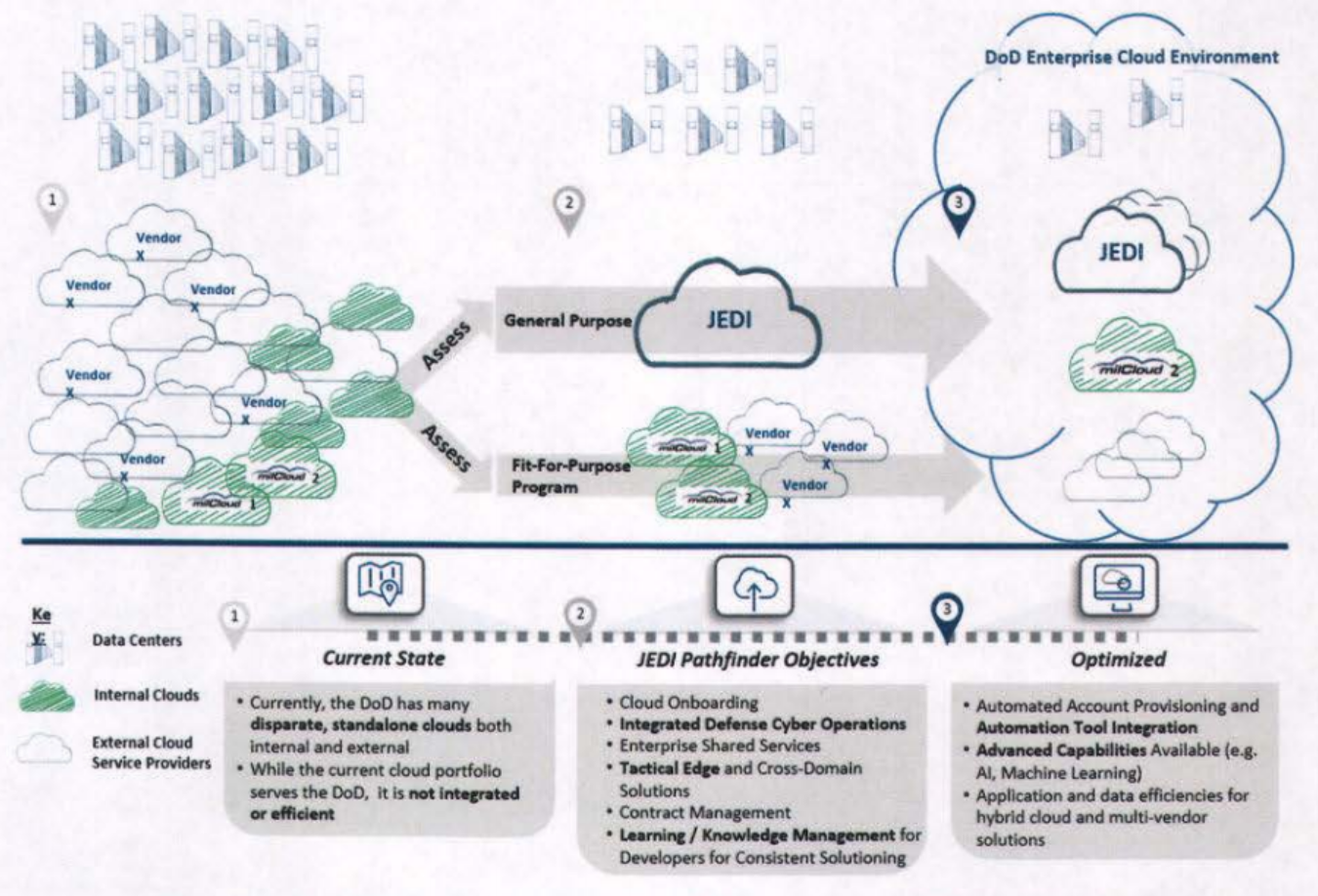 DoD Pathfinder to Hybrid Cloud Environments and Multiple Vendors
DoD Pathfinder to Hybrid Cloud Environments and Multiple Vendors
Our Major Tom software is cloud-native, meaning it is purpose built for the cloud model, and it provides a consistent development and automated management experience across all cloud infrastructures (private, public, and hybrid). In short, an enterprise can build applications that run on any cloud without modification. Image for post Image for post Credit: Deloitte
Moving back to the question of security of cloud technology, Consider this: a recent Deloitte survey of more than 500 C-suite executives, business unit leaders, managers, and programmers reveals that security and data protection is actually the top driver for initiating migration to the cloud. This may seem counterintuitive granted that many are under the notion that the cloud is not secure. However, cybersecurity attacks are rising in sophistication, and a shortage of skills means that many companies struggle to manage security in-house.
Executives and leaders are turning to third-party cloud and managed security services, with cloud providers offering complex and sophisticated cyber solutions that help significantly to mitigate security concerns. Another fact to point out from the Deloitte survey is that 91 percent of respondents said that their companies store data primarily on the cloud. Even more, 57 percent of the surveyed organizations’ businesses operate fully on the cloud — meaning that all of their applications and data are on it. Industry executives and leaders evidently see cloud as the key to modernizing their companies’ data-based technologies, and organizations are generally optimistic about data modernization even if some organizations don’t currently have formalized plans for data modernization or cloud migration.
Cloud technology is modernizing data platforms across all industries, and it is helping us push forward the boundaries of analysis, experimentation, and achievement. It has been the cornerstone of the CIA’s and Department of Defense’s largest and most significant IT redesigns, all the while still holding a perception by the general IT public of lacking security.
Leaps and bounds have been made by cloud technology service providers to ensure strength in cybersecurity, and regulatory mandates have been set in place to ensure organizations engage only with service providers who are in compliance with the required cybersecurity standards. Highly regulated industries, such as the space industry that Kubos operates in, tend to be laggards in adopting frontier-expanding technologies.
According to a Deloitte survey, 19 percent of respondents from the technology, media, and telecommunications (TMT) industry have either not begun data modernization or have only begun planning for data modernization. However, corporate executives, government leaders, defense leaders, and developers understand that cloud technology is a positive force in driving our global computing power forward, and in realizing immense technological advances.
The JEDI contract between the DoD and Microsoft is the most significant recent evidence of understanding. Kubos is bringing cloud technology to space. Our company is making it more cost effective for operators and spacecraft builders to build and operate their satellite constellation.
Furthermore, Kubos is following the strict guidelines of regulatory bodies as well as the research of leading cybersecurity experts to make sure the data related to missions are secure, and to make sure the user experience of our software is robust, intuitive, and cohesive. As the cost basis of space-related missions comes down, more missions — and more impactful missions — become viable, the industry grows, and our world advances.
There’s a reason why the DoD, the CIA, and major blue-chip corporations have adopted cloud technology early as a core part of their operations:

“Victorious warriors win first and then go to war, while defeated warriors go to war first and then seek to win” Sun Tzu, The Art of War
Author Simon Halpern is the Chief Operating Officer at Kubos Corporation.

