The transition of the Defense Security Service into the Defense Counterintelligence and Security Agency (DCSA) has involved integration of new missions, including background investiga-tions, and expansion of our security training enterprise. Even as we transition, we remain dedicated to securing the National Industrial Base (NIB) as part of our mission to strengthen national security and provide risk management services. As such, DCSA continues to work with cleared industry to detect and deter foreign entities' attempts to illicitly acquire classified and sensitive information and technology.

Securing the NIB is more relevant and more challenging than ever as our nation faces the most significant, diverse, and resourceful foreign intelligence threat it has ever experienced. The DCSA transition goes beyond new missions to include the development and implementation of new methodologies to secure the NIB. DCSA's new methodology is data-driven, risk informed, and partner-enabled. DCSA continues to move toward National Industrial Security Program compliance coupled with an asset-focused and threat-driven oversight methodology.
In protecting assets -such as the technologies, information, and personnel at cleared facilities -it is important to identify the threats, determine vulnerabilities, and implement appropriate countermeasures. These factors are essential in developing and successfully applying tailored security plans to protect assets at cleared facilities.
DCSA's annual report, Targeting U.S. Technologies: A Report of Foreign Targeting of Cleared Industry, is a key resource that identifies and describes the threat foreign entities pose to critical technologies and classified information in the hands of cleared industry. I encourage you to use this report as one tool in your risk management toolbox in determining strategies to mitigate risks to critical assets.
Charles S. Phalen, Jr., Acting Director
Defense Counterintelligence and Security Agency
SECTION 1: BACKGROUND
Scope During fiscal year 2018 (FYl8), the approximately 13,000 cleared contractor facilities reported 6,026 incidents that the Defense Counterintelligence and Security Agency (DCSA) considered a suspicious contact report (SCR). An SCR is a report DCSA receives from cleared industry that contains indicators that are either likely, almost certain, or for which there is an even chance that an individual, regardless of nationality, attempted to obtain unauthorized access to sensitive or classified information and technology or compromise a cleared employee.
These 6,026 reports are the basis for the numeric listing of foreign intelligence entitles (FIE)1 targeting of cleared industry. In addition, we include case studies and assessments of foreign entitles targeting U.S. technologies based on publicly available sources to augment the data and provide examples of foreign collection targeting cleared industry. The primary source of these case studies is the Department of Justice press releases published following the unsealing of indictments or following adjudication of cases. In case studies based on indictments, these contain allegations that a defendant has committed a crime. These defendants are presumed to be innocent until and unless proven guilty in court. Although some of the actual incidents used in the case studies did not occur in FYl8, the tactics described in the case studies remain relevant.
Assessing Foreign Intelligence Entity Threat to Cleared Industry This article details and enumerates cleared industry's reporting of SCRs that represent potential FIE attempts to illicitly acquire U.S. technologies resident in cleared industry. As an unclassified product, this report does not provide a holistic view of the FIE threat to cleared industry. An SCR from cleared industry represents an incident where a cleared facility's security protocols identified a potential FIE attempt to collect on U.S. technology. Therefore, an SCR, along with demonstrating FIE targeting to some extent also represents a success for a facility's security posture and its Counterintelligence (Cl) awareness and reporting regimen. DCSA cannot estimate in this forum the volume or targets of FIE activity that go unnoticed or unreported by cleared industry. DCSA annually produces a companion report at the classified level — Targeting U.S. Technologies: An Assessment of Threats to Cleared Industry.
Counterintelligence Awareness and Training
DCSA Counterintelligence Directorate has unclassified outreach products that provide information on Cl topics. They are available on the DCSA homepage: https://www.dcsa.mil/
The Center for Development of Security Excellence (COSE) provides diverse security courses and products to Department of Defense (DoD) personnel, DoD contractors, employees of other federal agencies, and selected foreign governments. CDSE content and course information is available at their web site: https://www.cdse.edu/
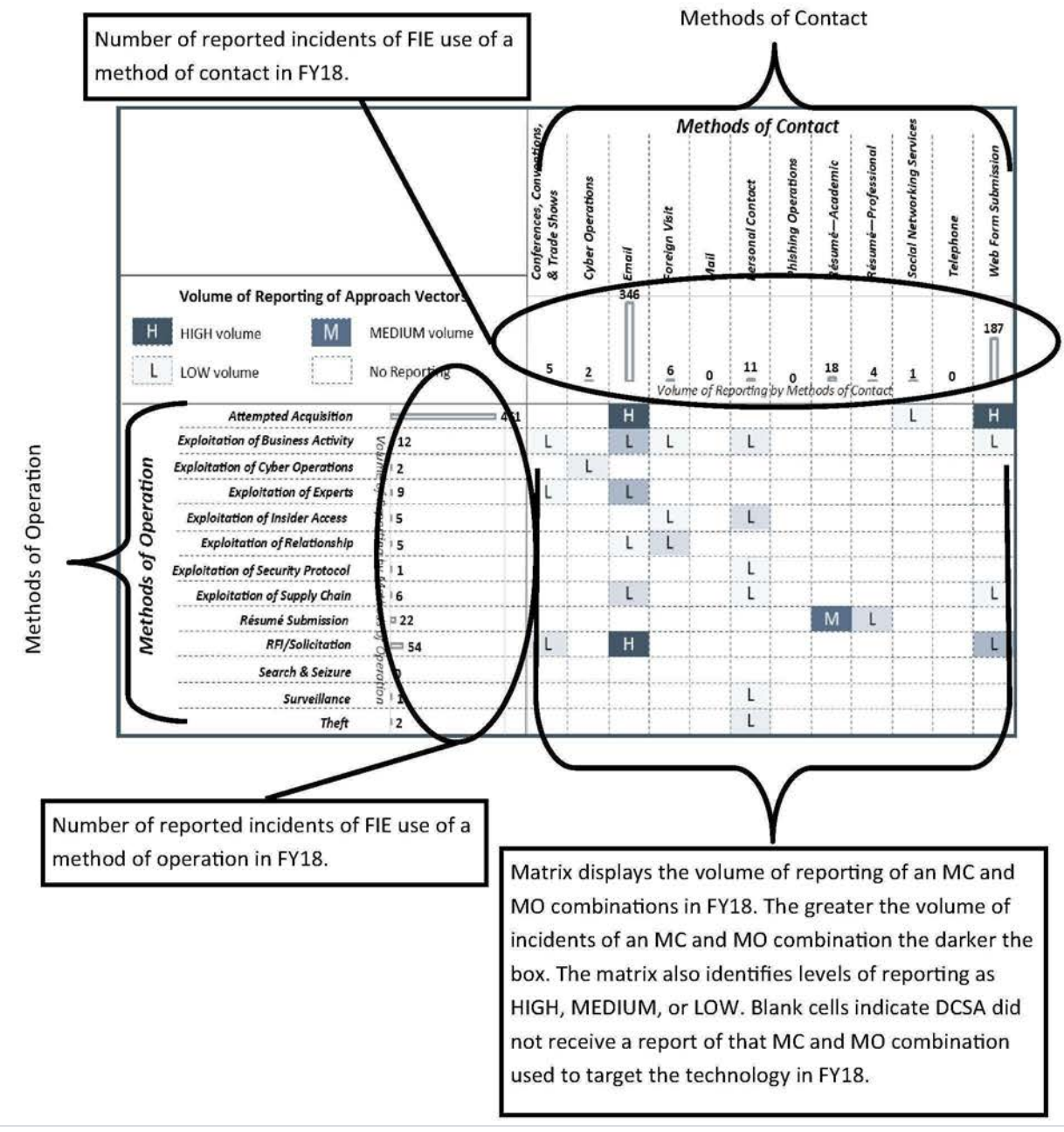
Displaying FIE Methods of Targeting Technology in Cleared Industry
Foreign entities use approach vectors that include a method of operation (MO) paired with a method of contact (MC) to attempt to illicitly obtain access to information and technology. The graphic below is an example of a matrix of FIE approaches, commonly referred to as the MCMO or 12x13 matrix (12 MCs x 13 MOs). This matrix depicts the volume of reported incidents of targeting of a specific technology in FY18. It displays the MCs and MOs used in incidents reported by cleared industry in FY18, which were likely attempts to illicitly gain access to technology, information, or cleared employees at the facility.
SECTION 2: EXECUTIVE SUMMARY
In FY18, DCSA received nearly 50,000 reports of suspicious activities from cleared facilities operating as part of the National Indus-trial Security Program (NISP). Of these, DCSA Cl Special Agents and Intelligence Analysts reviewed and identified 6,026 as incidents of Cl concern (considered SCRs) that are likely incidents of a foreign entity attempting to illicitly obtain information or technology resident in cleared industry, or an attempt to compromise a cleared employee. These reports are the basis for ranking FIE targeting of U.S. technologies resident in cleared industry.
Key Findings from FY18 Cleared Industry Reporting
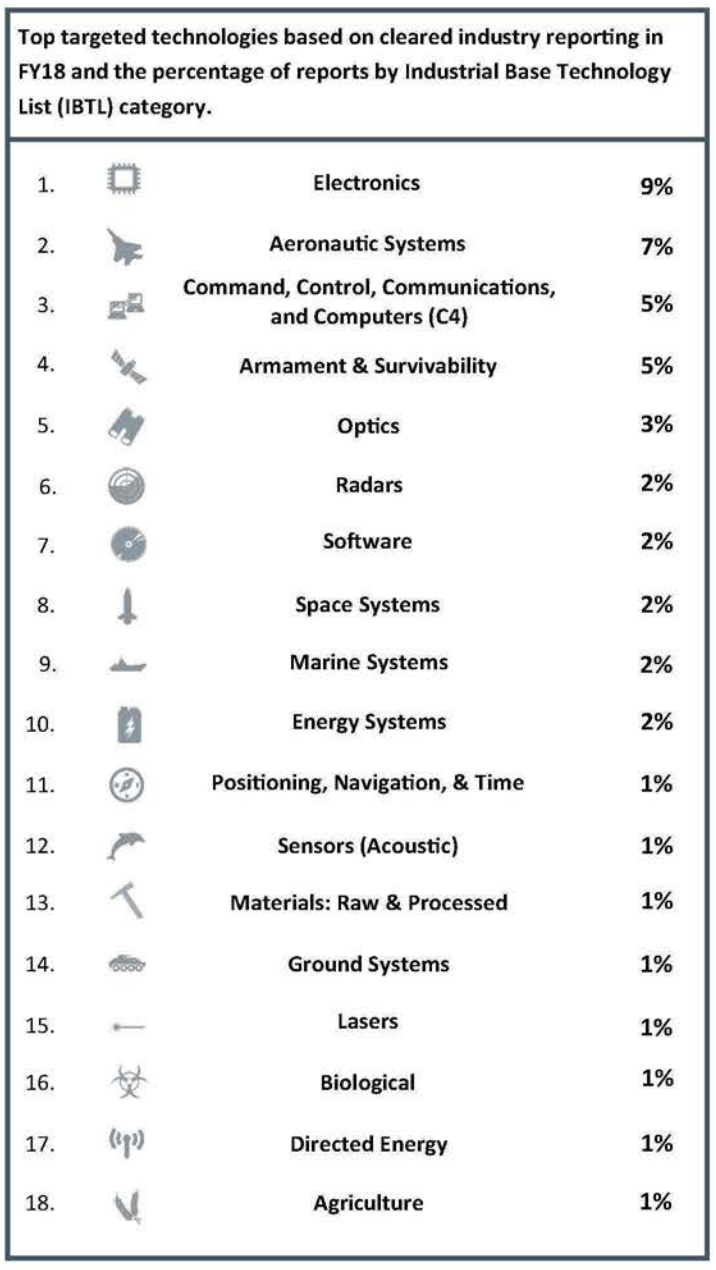
Other technologies targeted in less than 1 percent of cleared industry re-parting each: Manufacturing Equipment & Manufacturing Process; Nuclear; Chemical; Medical; Quantum Systems; Nanotechnology; Energetic Materials; Cognitive Neuroscience; Signature Control. Technologies with no reported targeting in FY18: Computational Modeling of Human Behavior, and Synthetic Biology.
• The number of reports assessed to be a suspicious contact increased by 3 percent over FY17
• The top four most targeted technologies in FY18 were in the top five most targeted technologies in FY17
• Optics was the fifth most targeted technology; previously it had not been one of the top five
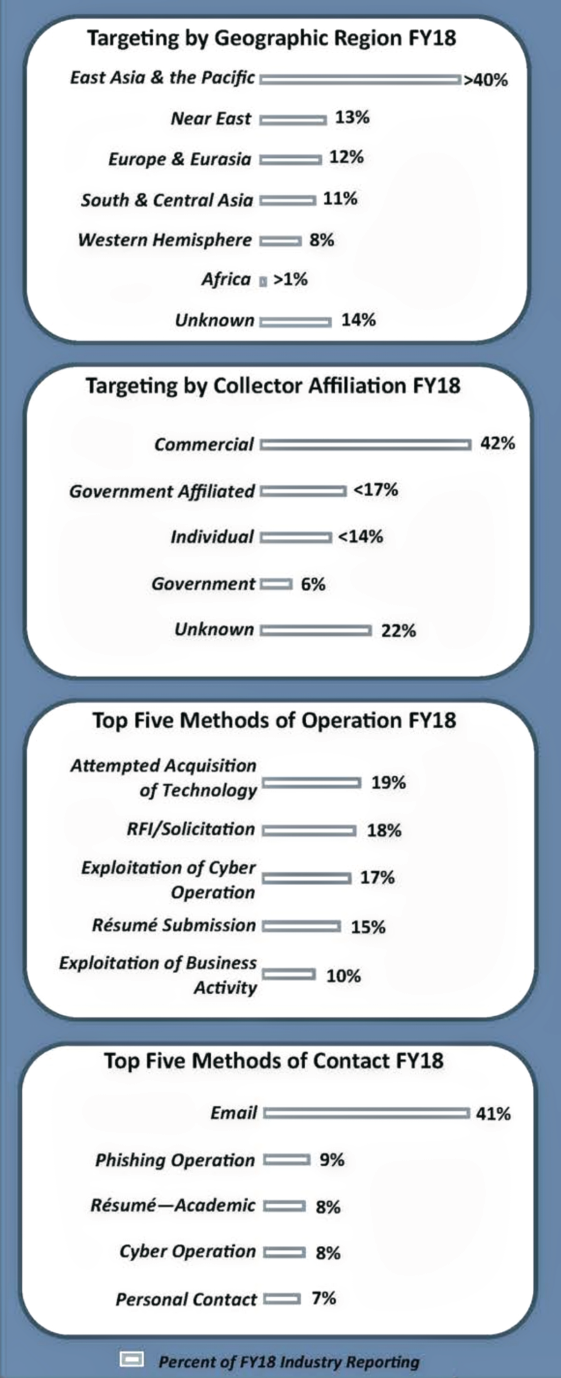
• East Asia and the Pacific was the most commonly identified origin of incidents reported by cleared industry
• Attempted acquisition of technology was the most common MO
• Exploitation of cyber operations increased by 55 percent in FY18
• Email was the most common MC used in 41 percent of the reported incidents
• Phishing operation was the second most common MC used in 9 percent of the incidents
• Cleared industry reporting also noted foreign collection targeting services provided by cleared industry
Overview
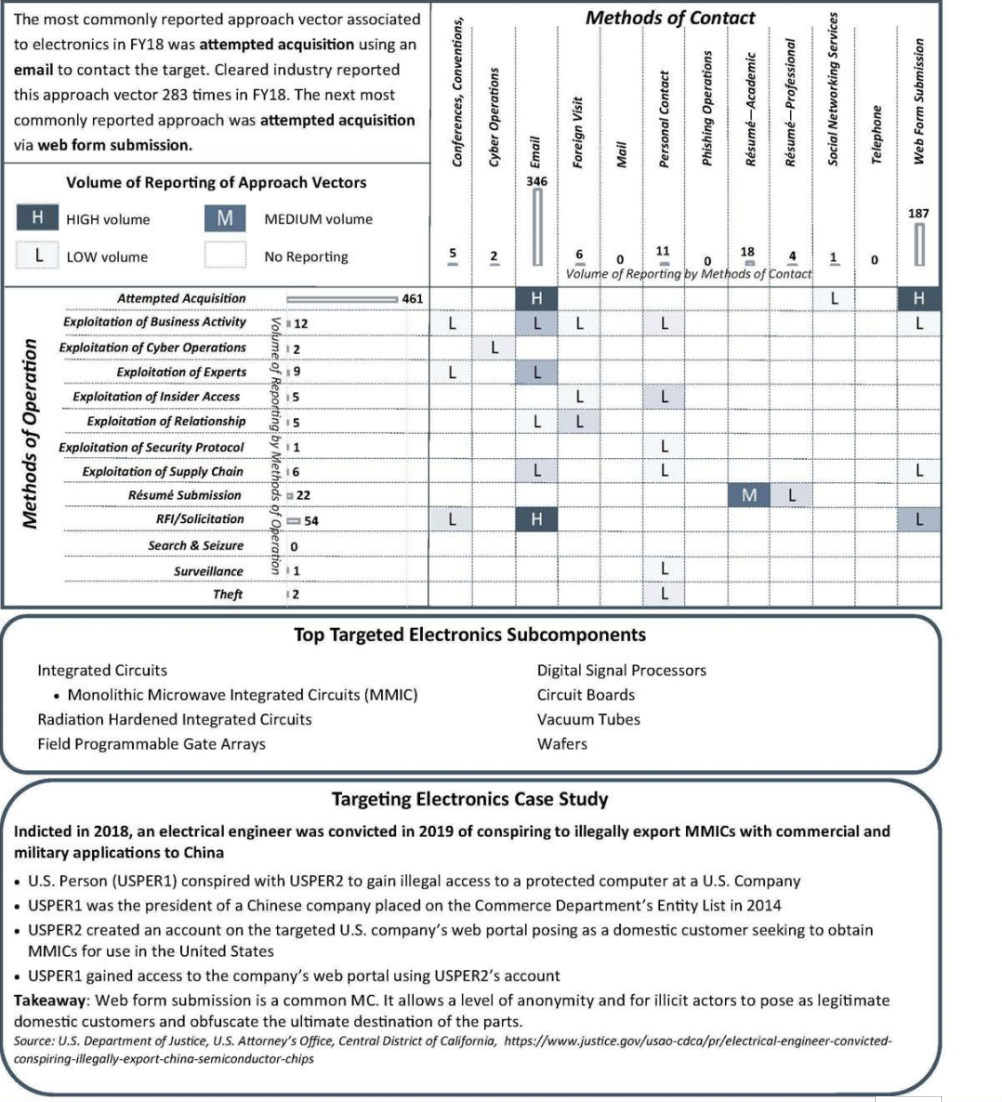
Overall reporting that DCSA categorized as a suspicious contact report increased by 3 percent in FY18. Reports where the specific technology or Industrial Base Technology List (IBTL) could not be identified amounted to 49 percent of the reporting. This is up from 40 percent in FY17. Electronics was the IBTL category that experienced the greatest increase in volume of reported targeting. Reported targeting of electronics increased by 73 percent in FY18.
Electronics were the most targeted technologies in FY18. Integrated circuits were the most targeted category of electronics.
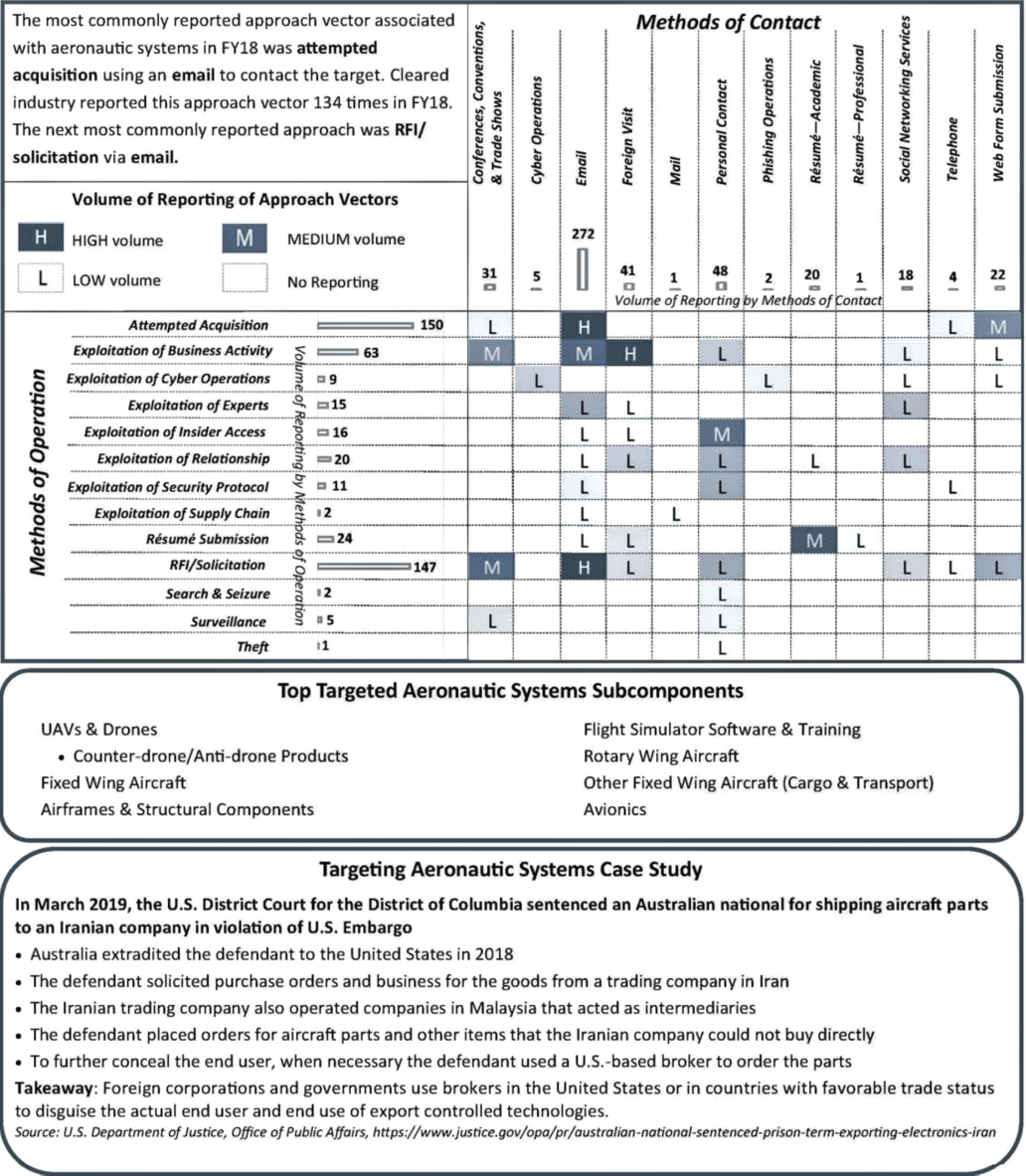
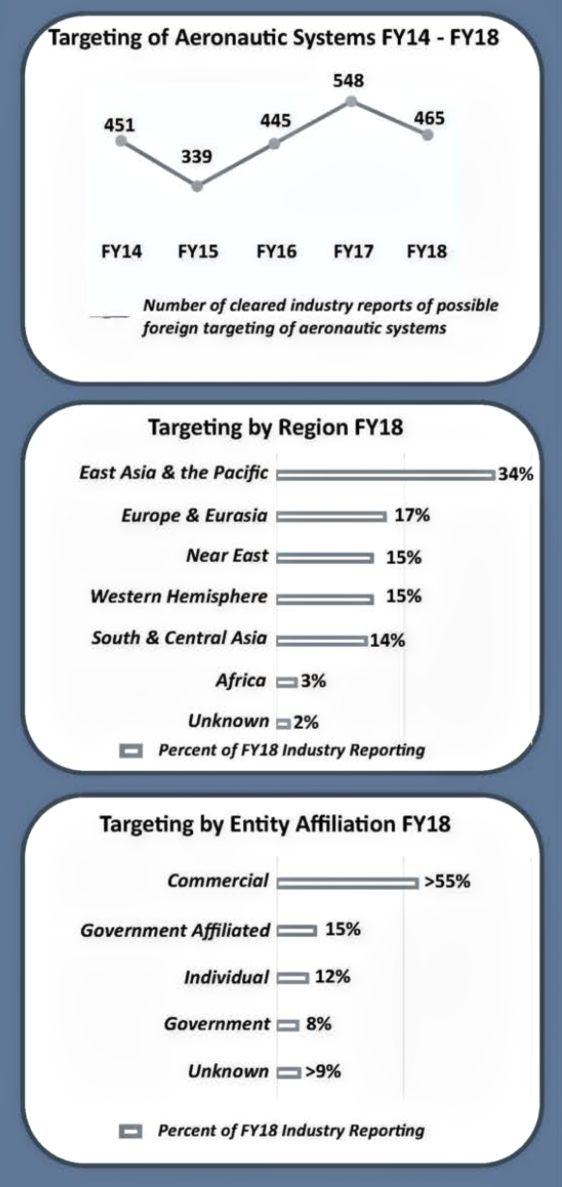
Aeronautics systems dropped from being the most targeted in FY17 to second most targeted in FY18. Aeronautics systems experienced a 15 percent decrease in targeting in FY18. Actors targeting aeronautic systems most commonly sought Unmanned Aerial Vehicles (UAV) technology and information.
Along with UAVs and drones, unmanned or independent systems were commonly targeted across technology sectors. Artificial intelligence was a highly targeted software. In marine systems, FIE targeted autonomous underwater vehicles and unmanned surface vessels technology. Similarly, unmanned ground systems technology was also targeted.
In FY18, cleared industry identified entities from East Asia and the Pacific region in more than 40 percent of reporting. The volume of reporting DCSA associated to entities in East Asia and the Pacific increased by 20 percent in FY18. Entities from this region were identified in over half of the incidents targeting electronics and a third of the incidents targeting aeronautic systems.
China, an East Asia and the Pacific region country, has been cited in multiple U.S. Government investigations and initiatives as having policies for technology transfer and intellectual property theft that pose a threat to U.S. economic security.
The Near East remained the second most active collector in FY18; even with a 37 percent decrease in the number or reports associated to entities from this region. Entities from this region most commonly targeted aeronautic systems and armament and survivability technologies.
The Near East remained the second most active collector in FY18; even with a 37 percent decrease in the number or reports associated to entities from this region. Entities from this region most commonly targeted aeronautic systems and armament and survivability technologies.
Cleared industry reporting in FY18 identified commercial entities as the collector in 42 percent of all reports. These entities used attempted acquisition of technology MO in approximately 35 percent of reported collection attempts. In addition, these entities relied heavily on email as the MC, using email in nearly 72 percent of these attempts.
FIE applied attempted acquisition of technology, request for information (RFl)/solicitation, or exploitation of cyber operations in 54 percent of incidents in FY18. Most of these attempts were accomplished remotely via email and web form submission, not requiring the collector to have direct contact with the target or even be in the United States.
Exploitation of cyber activity increased by 55 percent in FY18. Although in overall data it was one of the top MOs the origin of the incident and the specific targeted technology are often unknown.
Email was overwhelmingly the most common MC used in FY18 by FIE targeting cleared industry. Cleared industry cited email in 41 percent of the reports. This does not include the 9 percent of FY18 reporting which listed the MC as phishing operation, which is an attempt to send malicious code via an email. Combining email and phishing operation, cleared industry received half of all incidents via email.
FIE use approach vectors in their collection attempts. An approach vector includes an MO, the method the actor uses to obtain the information, with an MC, the method the actor uses to contact the target. The most common approach vector in FY18 was attempted acquisition of technology sent via email.
SECTION 3: TARGETING OF TECHNOLOGIES
Reported foreign targeting of electronics
Electronics is the study and engineering of electrical circuits and components. Electronics are the building blocks for almost all
technologies, and each system may contain hundreds if not thousands of electronics performing a specific function to ensure the operation of a system. Electronics includes, but is not limited to, integrated circuits, programmable memory, and wafers.
Key Findings from FYI Cleared Industry Reporting
• Electronics was the most targeted technology category in FY18
• Reported targeting of electronics increased by 73 percent over FY17
• East Asia and the Pacific region was the origin of most reported targeting of electronics
• Attempted acquisition of technology was the most common MO and email was the most common MC used to contact industry in attempts to target electronics
Overview
For each of the past 7 years, electronics has been one of the top three targeted technologies based on cleared industry reporting of suspicious contacts by foreign entities. Integrated circuits, primarily monolithic microwave integrated circuits, were the most targeted subcomponents in FY18.
In FY18, cleared industry reporting identified entities from East Asia and the Pacific region in over half of the incidents involving electronics. Reported incidents of targeting of electronics by entities from the East Asia and the Pacific region increased by 192 percent in FY18 compared to FY17. Electronics has been the top targeted technology by this region in 4 of the past 5 years. In FY18, their targeting included integrated circuits, radiation hardened (RADHARD) integrated circuits, digital signal processors, and circuit boards.
South and Central Asia entities were the second most active collectors targeting electronics. Entities from this region targeted integrated circuits, RADHARD, and field programmable gate arrays (FPGA). Entities from Europe and Eurasia were the third most active and targeted integrated circuits, FPGAs, and wafers.
Cleared industry identified commercial entities in three quarters of the incidents involving electronics. Commercial was the most common affiliation targeting electronics from all six of the geographic regions.
In FY18, entities targeting electronics used the attempted acquisition of technology MO in 79 percent of the reported incidents. Email was the most common MC, used in 60 percent of the incidents.
Takeaway
Cleared facilities developing or applying leading edge and legacy electronics technologies are reporting incidents of foreign entities targeting electronics in a greater volume than any other technology category. Integrated circuits, especially with special use properties such as radiation hardening, are highly sought after. The electronics sector is also vulnerable to counterfeit and substandard parts entering the supply chain.
Reported Foreign Targeting of Aeronautic Systems
Aeronautic systems include combat and non-combat air vehicle design and capabilities. This category does not include armament and survivability, C4, and intelligence, reconnaissance, and surveillance (ISR) technologies that may be added to aeronautic systems for a specific combat or non-combat role. Aeronautic systems includes, but is not limited to, fixed and rotary wing aircraft and design, UAV, and airframes.
Key Findings from FY18 Cleared Industry Reporting
• Aeronautic systems was the second most targeted technology category in FY18
• Reported targeting of aeronautic systems decreased by 15 percent from FY17
• East Asia and the Pacific region was the origin of most reported targeting of aeronautic systems
• Attempted acquisition of technology was the most common MO and email was the most common MC used to contact industry in attempts to target aeronautic systems
Overview
For each of the past 6 years, aeronautic systems has been one of the top three targeted technologies based on cleared industry reporting of suspicious contacts by foreign entities. Unmanned aerial vehicles and drones, notably counter-drone/ anti-drone products, were the most targeted aeronautic systems technologies in FY18.
In FY18, cleared industry reporting identified entities from East Asia and the Pacific region in over a third of the incidents involving aeronautic systems. Reported incidents of targeting of aeronautic systems by entities from the East Asia and the Pacific region decreased by 8 percent in FY18 compared to FY17. Entities from this region targeted UAV and drone tech-nologies commonly seeking UAV transponder or counter-UAV technologies.
Europe and Eurasia entities were the second most active collectors targeting aeronautic systems. Entities from this region also targeted UAVs and drones, as well as fixed wing aircraft technologies. Entities from the Near East and Western Hemisphere regions were equally active collectors of aeronautic systems technologies in FY18.
Cleared industry identified commercial entities in over half of the incidents involving aeronautic systems. Commercial was the most common affiliation targeting aeronautic systems from all six of the geographic regions.
In FY18, entities targeting aeronautic systems used the attempted acquisition of technology and the RFl/solicitation MO each in 32 percent of the reported incidents. Email was the most common MC, used in 58 percent of the incidents.
Takeaway
The United States is a leader in this technology field and will remain a target as other countries plan to develop peer capabilities. In addition, aeronautic systems tech-nology is vital in developing force projection, reconnaissance and surveillance, and air dominance capabilities.
Foreign Collection Methodology Targeting Aeronautic Systems
Foreign entities use approach vectors that include an MO paired with an MC. The matrix below depicts the volume of reported incidents of targeting aeronautic systems in FY18.
Reported foreign targeting of command, control, communication, and computers
C4 is the backbone of almost all government functions -from battlefield commanders to interagency communications. Monitors, computers, printers, phones, radios, and data links are all necessary in this network centric environment. C4 includes, but is not limited
to, computers and central processing units (CPU), common data links, telecommunication devices, and antenna.
Key Findings from FY18 Cleared Industry Reporting
• Each year since FY13, C4 has been one of the top three targeted technology categories
• Reported foreign targeting of C4 technologies decreased by 27 percent in FY18 when compared to FY17
• Entities from East Asia and the Pacific region were the most active collectors of C4 technologies identified in cleared industry reporting in FY18
• These collectors contacted cleared industry via email in 63 percent of reported incidents
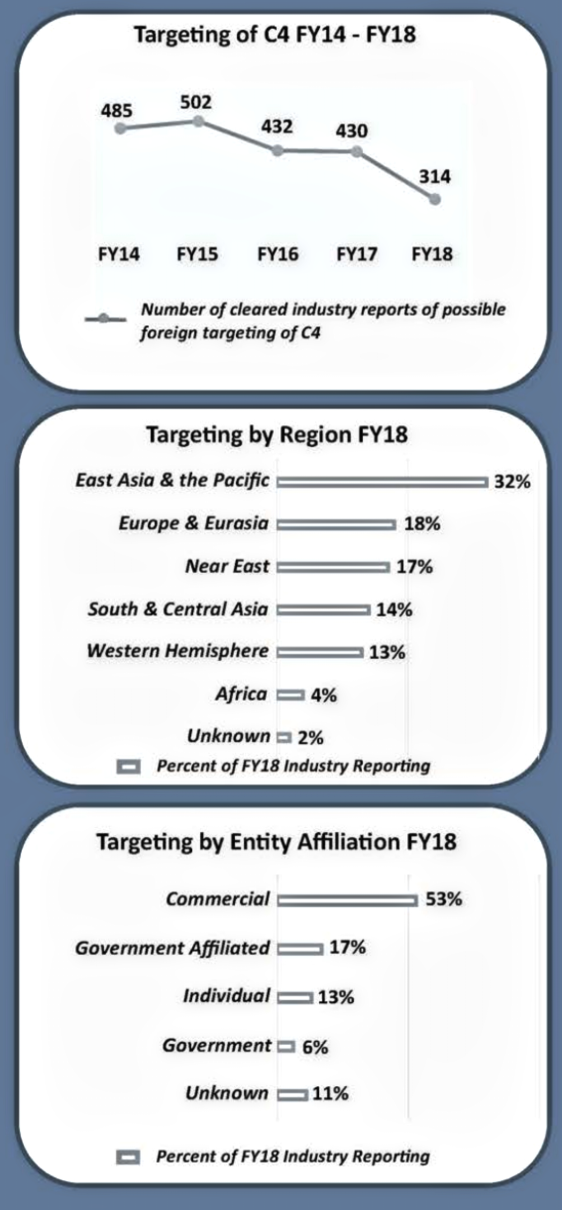
Overview
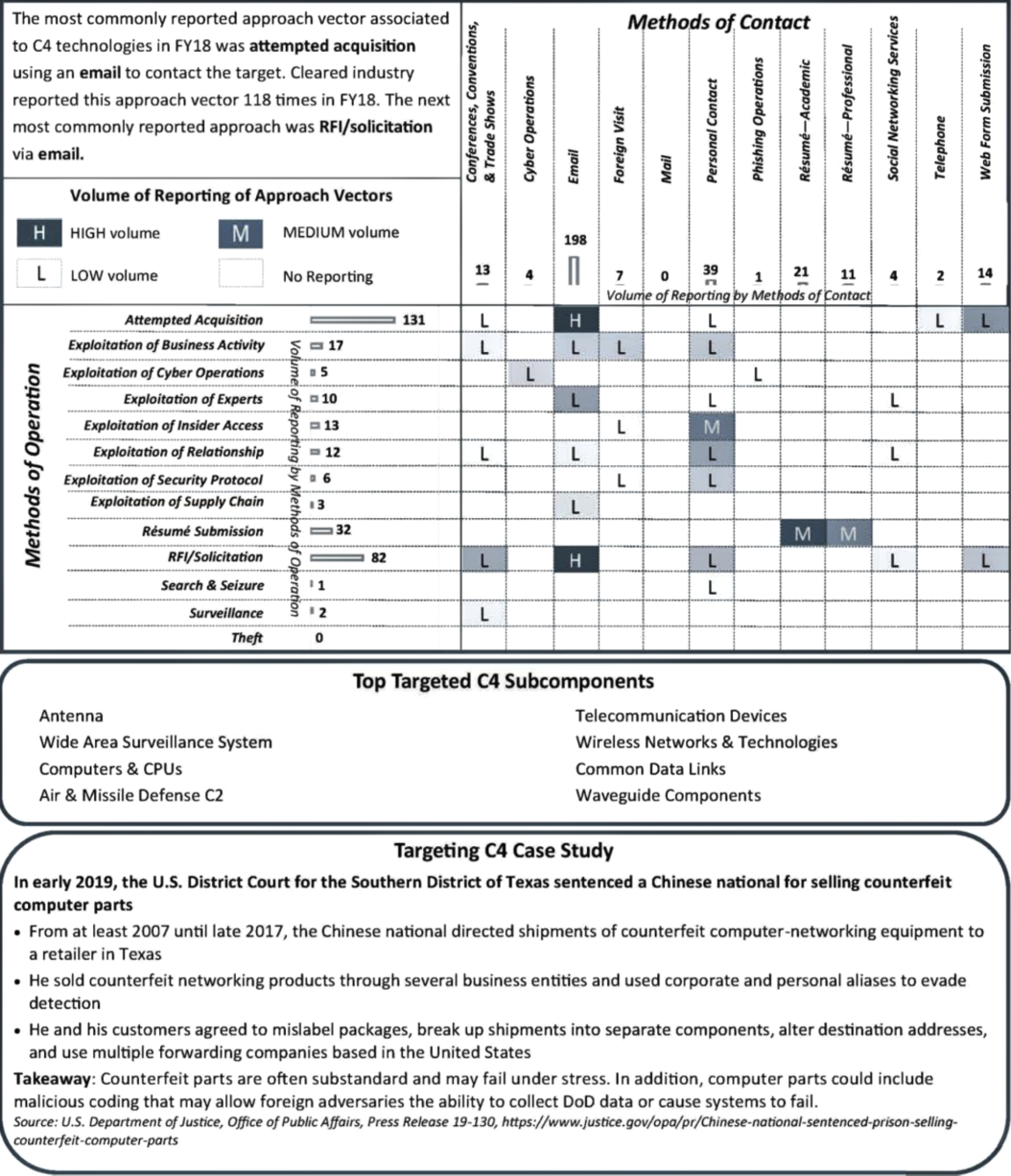
With the decrease of 27 percent in targeting in FY18, C4 dropped from the second to the third most commonly targeted technology as identified in cleared industry reporting. Industry reported fewer attempts to target highly sought after C4 components such as antennas, telecommunication devices, computers and CPUs, and common data links. Conversely, reporting identified an increase of incidents relating to wide area surveillance systems and wireless networks and technologies.
In FY18, cleared industry reporting identified entities from East Asia and the Pacific region in 32 percent of the incidents involving C4. Reported incidents of targeting of C4 by entities from the East Asia and the Pacific region increased by 1 percent in FY18 compared to FY17. Entities from this region targeted C4 components such as antennas, wireless networks and technolo-gies, and wide area surveillance systems. In FY17, this region was the second most active region after the Near East region.
Europe and Eurasia entities were the second most active collectors targeting C4 in FY18. Entities from this region targeted telecommunication devices, wide area networks and technologies, computers, and CPUs.
In FY18, commercial entities were identified in over half of the reported incidents of targeting of C4 technologies. This was the most common affiliation targeting C4 from all geographic regions except the Western Hemisphere, in which individual was the most common collector affiliation.
In FY18, entities targeting C4 most frequently used the attempted acquisition of technology MO and email was the most frequently used MC.
Takeaway
C4 technologies are highly sought after by foreign collectors. Beyond targeting industry for sensitive technologies, foreign entities also attempt to provide counterfeit computer parts to U.S.
companies that could subsequently enter DoD supply chains. Counterfeit parts could fail due to substandard quality or by design; either could negatively impact the warfighter.
Foreign collection methodolgy targeting C4
Foreign entities use approach vectors that include an MO paired with an MC. The matrix below depicts the volume of reported incidents of targeting C4 in FY18.