No Cost Involved To U.S.A.F. For SBIRS Update
The U.S. Air Force’s newest infrared surveillance and missile warning satellites will be based on Lockheed Martin’s modernized A2100 spacecraft, an update that improves system affordability and resiliency while also adding the flexibility to use future payloads

Artistic rendition of the Space Based Infrared System (SBIRS. Image is courtesy of Lockheed Martin.
The fifth and sixth Space Based Infrared System (SBIRS) Geosynchronous Earth Orbit (GEO) satellites will receive this advanced spacecraft technology at no additional cost to the existing fixed-price contract.
The SBIRS program is responsible for America’s early missile warning and infrared surveillance missions, which are crucial to global security.
In response to the Department of Defense’s need for more affordable and resilient systems, the U.S. Air Force and Lockheed Martin worked to add the A2100 bus update to the 2014 SBIRS block-buy contract, which already saved the U.S.A.F. more than $1 billion.
The modernized A2100 adds further affordability by using common components, streamlined manufacturing and has a flexible design that reduces the cost to incorporate future, modernized sensor suites. The modernized A2100 builds on a flight-proven bus that is the foundation for more than 40 satellites in orbit today.
Through an internally-funded, multi-year modernization effort, Lockheed Martin has enhanced the spacecraft’s power, propulsion and electronics, while also adopting the latest advanced manufacturing techniques to decrease production costs and timelines.
“Through the leadership of the Air Force’s Space and Missile Systems Center, we have been working to address the Department of Defense’s Better Buying Power and Bending the Cost Curve initiatives to deliver more value per dollar on this vital national security system,” said David Sheridan, Lockheed Martin vice president and SBIRS program manager. “SBIRS has been providing outstanding global coverage for the Air Force, and migration to the modernized A2100 will help keep SBIRS ahead of America’s adversaries while dramatically reducing costs and cycle times.”
www.lockheedmartin.com/us/products/sbirs.html
NATO’s Global Hawks
Expanding NATO’s joint intelligence, surveillance and reconnaissance (ISR) capability, Northrop Grumman Corporation and its industry partners together with NATO leaders have unveiled the first NATO Alliance Ground Surveillance (AGS) aircraft to an audience of customers, distinguished guests, employees and community leaders.
The unmanned aircraft, a wide area surveillance Global Hawk, is part of a broader system of systems solution that will advance the Alliance’s evolving ISR needs during a full range of NATO’s missions such as protection of ground troops and civilian populations, border control and maritime safety, the fight against terrorism, crisis management and humanitarian assistance in natural disasters.
The NATO-owned and operated program comprises five air vehicles and fixed, mobile and transportable ground stations. Northrop Grumman’s primary industrial team includes Airbus Defence and Space (Germany), Selex ES (Italy) and Kongsberg (Norway), as well as leading defense companies from all participating countries.
With the ability to fly for up to 30 hours at a time, the high-altitude long-endurance system will provide NATO leaders with persistent global situational awareness. The aircraft is equipped with leading-edge technology, including the Multi-Platform Radar Technology Insertion Program (MP-RTIP) sensor. The MP-RTIP will provide critical data to commanders during operations in any weather, day or night. The NATO AGS system will also be able to fuse sensor data, continuously detect and track moving objects and provide detailed imagery.
The industries of the 15 participating nations (Bulgaria, Czech Republic, Denmark, Estonia, Germany, Italy, Latvia, Lithuania, Luxembourg, Norway, Poland, Romania, Slovakia, Slovenia and the United States), are each contributing to the delivery of the AGS system. All 28 Alliance nations will take part in the long-term support of the program.
The U.S. Army To focus On Cyber Strategy In Tactical Environments
The Army is analyzing cyberspace requirements and outlining potential technical investments based on its Cyber Materiel Development Strategy, released earlier this year.

Doctrinal, operational, acquisition and research and development communities, for Army materiel development, worked together for more than two years on the comprehensive strategy, which looks at where Army cyberspace capabilities are and what lies ahead.
“The Army must be prepared to operate and fight within the cyberspace domain,” said Assistant Secretary of the Army for Acquisition, Logistics and Technology Heidi Shyu. “It is essential... that we use our limited acquisition and science and technology resources to identify and address critical Army specific problem sets and capability gaps. Where possible, we must leverage the best solutions and ideas available through our partnerships and collaboration within the Department of Defense, other government agencies, industry and academia.”
Shyu appointed Henry Muller, director of the U.S. Army Communications-Electronics Research, Development and Engineering Center, or CERDEC, as the Army Cyber Task Force lead.
“In less than two decades, cyberspace has radically transformed how the Army operates and wages war,” Muller said. “Unlike the other physical domains, cyberspace will continue to grow and is projected to reach over 100 billion connected devices within just the next 10 years.”
“These monetary and technological investments may determine how dominant the Army will remain in the future,” Muller said
The Department of Defense has identified cyber as an operational domain much like air, land, maritime and space; however, no military service has been assigned the cyber domain. Additionally, the Army still operates in a fiscally-constrained environment, where spending and allocation of resources cannot address all aspects of cyber, said Giorgio Bertoli, CERDEC Intelligence and Information Warfare Directorate, acting chief scientist and lead action officer for the strategy.
“Cyber is hard to predict,” Bertoli said. “One of the challenges is the technology turnover rate is very high. Adoption for new technology is also increasing as the public becomes more and more comfortable embracing new technological advancements.”
“You can predict that processing power is going to keep increasing; you can keep predicting bandwidth wired and wireless, is going to keep going up; you can predict new technologies like quantum computing will eventually come to pass,” Bertoli said. “The hard part to predict is how are they going to be used? What are the new applications these technical advances are going to enable?”
The Army identified that it needs to make advances in several Army-unique problem sets. One such area is the Army’s tactical operations center, where military specific operations occur. While its enterprise level network is similar to commercial businesses, the tactical network faces military-unique defensive and offensive challenges.
Tactical networks have limited bandwidth with high-bit error rates, high latency, intermittent connectivity, and roaming infrastructure and users.
“On top of that, you have other related data like mission command data that are passing over these very limited bandwidth channels to begin with. Any security you pass over these channels degrades what other traffic they can send,” said Steven Lucas, chief engineer, CERDEC Space and Terrestrial Communications Directorate, Cyber Security and Information Assurance Division.
The Army is unique in that it operates for extended periods within adversarial environments.
“We’re highly reliant on distributed communications systems, which are more prone to interception because you are in close proximity to the enemy within radio line of sight range,” Bertoli said.
One aspect of defending the tactical network includes intrusion detection.
“Intrusion detection allows a sensor to detect potentially malicious activity on a specific node, such as a handheld device or a laptop, and limit the user’s capabilities,” Lucas said.
“With respect to intrusion detection, you have sensors that are doing the detection of malicious activity, either on the network or at the host level, and whenever they detect something they feed it up to this higher authority,” Lucas said. “Because of our environment, that connection between the authority and the actual detector may not always be there.”
If the intrusion detection sensor spots potential malicious code on a handheld device, it might limit data transmission capabilities but still allow the Soldier to use the voice capabilities. The intrusion detection software would continue to monitor the device before determining if it needs to come off the network.
Another aspect of defending the network includes software assurance. Typically, one vendor does not develop code for single software application, but rather multiple vendors contribute to the code and then integrate it into one package.
CERDEC and the U.S. Army Research Laboratory have developed various techniques, such as fuzzing, to analyze binary code to identify potential holes in the software.
“Fuzzing is where you throw garbage at the executable code and try to get the software to do something that it wasn’t designed to do,” Lucas said. “Then through analysis, you can see if there was a buffer overflow or a memory leak where now it opens a potentially exploitable window into that software.”
From the research and development side, CERDEC wants to perform the majority of software analysis upfront before the system is fielded. Not only will it protect Soldiers from using vulnerable software, but it will also save the Army time and money in development and sustainment.
“Software analysis is a continuous process you need to do, and then we also have developed capabilities to where ultimately we don’t want to wait to the very end just before the application goes out to the field,” Lucas said. “Do it up front, do it during the actual coded development and writing, where you can ultimately save.”
Based on a calculation done on a mission command application, if a vulnerability in a system was found during the development cycle instead of the pre-deployment phase, the government could save roughly $30 million over the entire program lifecycle, he said.
An additional tactical concern is access control and identity management at all levels across the network, as there may be a mixture of cleared and uncleared users.
Most employees associated with the government are familiar with the Common Access Card, or CAC, which allows two-factor identification to gain access to government-issued computers.
This form of two-factor identification works adequately for stationary systems in an enterprise and non-dynamic environment, such as an office cubicle; however, a CAC is not the most practical access control and identity management tool for many environments, Lucas said.
“Ultimately how you come up with or maintain that trust consistently across the network is very hard to do,” Lucas said. “From a device perspective, the user needs to have trust in the device, which provides the information to them to make decisions. You want to ensure that nobody can just add a device of their own, like an enemy laptop, to the network. You want the devices themselves to be trusted.”
CERDEC is working with project managers and the chief information officer/G6 to research, design, develop, and test state-of-the-art identity management systems, which will work in the unique tactical environment.
The Army Cyber Strategy calls for the continued effort to further protect its tactical networks, but it also calls for research and development on how the Army can leverage its own sensors and exploit enemy capabilities.
“Offensive Cyberspace Operations provide a military commander a non-kinetic capability option that eliminates or minimizes the physical damage caused by other traditional forms of military engagement,” Bertoli said.
“One of the key things we’ve been pushing for a while now is that we need to do a better job of leveraging our tactical assets to improve CEMA [cyber electromagnetic activities] situational awareness,” Bertoli said.
As part of the strategy, the Army will continue to determine how it can best leverage sensors that are already in the field to enable such cyber capabilities.

To make these offensive and defensive advances, the Army needs to base its development on a modular and flexible architecture to ensure it can keep with the continually increasing advancements
in cyberspace.
It is impractical for the Army to chase after every new technology to defeat it; however, it is possible and fundamentally important to further develop architecture frameworks, which will minimize the amount of new code needed to deal with new technologies, Bertoli said.
“In order to achieve this, you need to have some pretty extensive laboratory infrastructure like we have here at APG [Aberdeen Proving Ground], and those labs have to be constantly updated to keep up with the churn of technology,” Bertoli said.
“Though a great first step, the Army is still working at defining its role and doctrine as related to cyberspace operations. This, coupled with the rapid pace of technical innovation within the domain will require the S&T [science and technology], operational, doctrinal and acquisition communities to maintain close working relationship and to ensure this strategy remains current,” Bertoli said.
Editor’s Note: This article originally appeared in the May/June 2015 issue of Army Technology Magazine (armytechnologymagazine.com/), which focuses on Future Computing.
New DigitalGlobe + Saab JV For 3D Geospatial Intelligence
Defense and security company Saab and DigitalGlobe, Inc. have created a joint venture—Vricon, Inc.—to produce photo-realistic 3D products and digital elevation models globally for enterprise and government geospatial markets with unmatched coverage and delivery timelines.
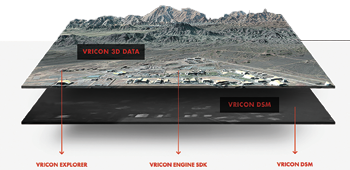
Vricon combines Saab’s unique 3D technology and know-how with DigitalGlobe’s unrivaled archive, which contains billions of square kilometers of the world’s highest quality commercial satellite imagery.
Together, the Vricon joint venture will establish high scale production capabilities that will make highly accurate photo-realistic 3D products and elevation data of the Earth, accessible via its unique visualization platform and standard based data formats.
Vricon serves the entire professional geospatial market, with an initial focus on defense, security, and infrastructure.
Vricon’s technology enables imagery content to accurately represent all visible objects on the Earth in 3D, and its products provide customers with unmatched value and utility, superior coverage relative to aerial-derived elevation models, and superior fidelity and availability relative to other satellite-derived models.
DigitalGlobe and Saab will combine their strengths to both support and own Vricon. Under the agreement, Vricon will be headquartered in Reston, Virginia, with ownership set up as 50 percent DigitalGlobe and 50 percent Saab.
“Our customers will benefit from global access to geospatial data of unprecedented quality. It is a win-win situation with long-term value creation for both parent companies, which will give us a market position ahead of competition,” said Magnus Brege, CEO at Vricon.
“By combining DigitalGlobe’s unrivaled imagery archive with Saab’s leading edge technology, we will deliver the globe in 3D at a scale never before possible,” said Jeffrey R. Tarr, DigitalGlobe President and Chief Executive Officer. “By delivering this breakthrough product to our customers, this collaboration will drive growth and shareowner value creation.”
“The establishment of Vricon is another great example of Saab’s ability to leverage innovation and transform it into business value,” said Dan Jangblad, Head of Saab business area Industrial Products and Services. “Together with DigitalGlobe, we are taking our revolutionary new 3D technology and applying it to benefit our global customer base. At the same time, we also take another step forward on our long-term path for growth in the United States.”
www.vricon.com/
digitalglobe.com/
saab.com/
CPI Offers NEW COTM Units
Communications & Power Industries (CPI) in Camarillo, California, has rolled-out their GMA-100QB antenna system to

link military ground vehicles with unmanned aircraft.
The GMA-100QB Communications-On-The-Move antenna (COTM) provides On-The-Move (OTM), Line Of Sight (LOS) bi-directional communications capability to link military vehicles to unmanned aerial systems (UAS) in L-, S-, C-, and Ku-bands.
Capable of Churchville B OTM performance, the GMA-100QB is equipped with high performance motors and drives on both axes to handle high dynamic loads.
The antenna is stabilized by internal AHRS, allowing independence from vehicle data. The receiver with built in received signal strength indicator (RSSI) enables the antenna to scan the sky rapidly for available signals and point to the desired airborne asset, eliminating the delay of external modem decoding of the signal. Embedded amplifiers on transmit/receive at all bands allow a full communications system with only the addition of external DC power and a modem.
The GMA-100QB includes a compact multiband high gain directional antenna array, enabling long range LOS datalinks, and a broadband omnidirectional antenna for close-in/overhead communications. Frequency band and antenna selection is electronically commanded.
General Dynamics Moving Ahead With WIN-T
The U.S. Army received approval to move forward with full rate production of the Warfighter Information Network – Tactical (WIN-T) Increment 2 system.

Designed and built by General Dynamics, WIN-T Increment 2 provides commanders and soldiers with an unprecedented ability to communicate, share information and intelligence while on patrol, with connectivity rivaling that found in a stationary command post.
The action follows an Acquisition Decision Memorandum (ADM) issued by the office of the U.S. Undersecretary of Defense for Acquisition, Technology and Logistics. The ADM authorizes the Army to proceed to full rate production and fielding of its mobile tactical communications backbone network to all remaining Army units projected to receive the WIN-T Increment 2 system through 2028.
“This is an important milestone and we’ll continue to support the Army as it fields this vital mission command and communications system throughout its global force,” said Chris Marzilli, president of General Dynamics Mission Systems.
WIN-T Increment 2 is integrated into Mine Resistant Ambush Protected (MRAP), High Mobility Multi-purpose Wheeled Vehicles (HMMWV) and Stryker vehicles. To date, four division headquarters and 12 brigade combat teams have WIN-T Increment 2.
The system successfully served Army units supporting the Security Force Assistance Brigades in Afghanistan by replacing the fixed communications infrastructure dismantled when the U.S. military closed its operating bases.
Last summer, WIN-T provided the ‘communications grid’ for humanitarian operations responding to the Ebola epidemic in
West Africa.
Production of the WIN-T system occurs primarily at General Dynamics’ facility in Taunton, Massachusetts, and supports hundreds of jobs at General Dynamics and supplier locations nationwide.
More information about WIN-T, tactical radios, satellite communications and the cyber-defense products that make up the Soldier’s Network is available at www.thesoldiersnetwork.com.





