Cyber-attacks, focused primarily on identity and financial theft in the commercial world, are becoming a critical issue in space.

Cyber-attacks on satellites can include jamming, denial of service (DoS), hacking attacks on communication networks and piracy. Piracy, or unauthorized access, occurs when carriers (with content) are transmitted toward a satellite without any prior contract with the satellite operator.
Intentional jamming can be the result of one party’s objection to the content (political, cultural, social, etc.) of the targeted carrier, extenuating circumstances (political situation, social unrest, etc.) and in the worst case, intent to disable a satellite to gain
a military or economic advantage.
Roots of Vulnerability
Unlike optical fiber or copper cables, satellites send their radio frequency (RF) signals through air and space, creating the opportunity for anyone with the appropriate knowledge, means and motivation to interfere with the RF signal.
Such interference can be accomplished by jamming, variations of which include blocking undesirable radio and television broadcasts from being transmitted into a country and blocking satellite navigation signals. Increasingly, with the use of Commercial-Off-The-Shelf (COTS) products such as open-source software, vulnerabilities are multiplied. It is one thing to protect proprietary products from latent malware being inserted during development, but the risk is compounded when acquiring the products from a long supply chain.
Another challenge is the speed with which technology advances, coupled with the fact that it can take two to three years to build and launch a satellite designed for a 10 to 15 year lifespan. In these cases, one not only has to embed cybersecurity defenses in the satellite during the design stage but must also be prepared to retro-fit on-orbit satellites with newer cyber defenses during the satellite’s life span.
Of all the vulnerabilities those with the most potential for severe disruption are satellite-based navigational systems… Galileo in Europe, BeiDou in China, GLONASS in Russia, the Indian Regional Navigation Satellite System (IRNSS), and the U.S. global positioning system (GPS), which is the most pervasive and supports much of the world’s civil infrastructure.
New Department of Defense Cybersecurity Strategy
The Department of Defense (DoD) recently issued their first cybersecurity strategy since 2015.
On the heels of that announcement, Patrick Shanahan, Department of Defense Deputy Secretary, made it known to the defense industrial base that he expects the products and services DoD buys to come secure, just as the department also expects them to be of the best quality.
The new cybersecurity strategy focuses on how the department will implement the priorities of its National Defense Strategy in cyberspace, particularly in defending against Russian and Chinese “persistent, aggressive cyberspace campaigns that pose strategic, long-term risks to the Nation, our allies, and partners.”
The strategy sets five objectives DoD will strive to achieve indefinitely into the future:
• Ensuring the Joint Force can achieve its missions in a contested cyberspace domain.
• Enhancing Joint Force military advantages through the integration of cyber capabilities into planning and operations.
• Deterring, preempting, or defeating malicious cyber activity targeting U.S. critical infrastructure that is likely to cause a significant cyber incident.
• Securing DoD information and systems, including on non-DoD-owned networks, against cyber espionage and malicious cyber activity.
• Expanding DoD cyber cooperation with allies, partners, and private sector entities.
Resilience, Agility and Speed
These vulnerabilities are driving change in military space, as well as in the commercial world and countering them requires more resilience, agility, and speed in order to predict, pre-empt, and prevent the growing range of threats.
 Artistic rendition of the U.S. Global Positioning Satellites on orbit around Earth.
Artistic rendition of the U.S. Global Positioning Satellites on orbit around Earth.
Aside from disruption of civil infrastructure, cyber-attacks on satellites could weaken responses to military threats, by compromising satellite command and control (C2), operational monitoring and payload performance.
As such, the DoD plans to spend $2 billion over the next five years on a new constellation of Global Positioning System satellites that will be hardened to withstand electronic interference from hostile nations, satellite ground systems need to be protected, as well.
In making the announcement U.S. Air Force Secretary Heather Wilson said the U.S. Air Force is motivated to move ahead with this new constellation amid increasing concerns that a growing number of nations are developing electronic weapons to jam or interfere with GPS signals.
“All those things are an obvious awareness of American dominance in space. I cannot think of a military mission that doesn’t depend on space. Our potential adversaries know it, and we need to protect those vital assets,” she said.
Also, in a move to enable Air Force Space Command to focus entirely on space superiority, the responsibility of fighting hackers in cyberspace has been transferred to Air Combat Command. According to Wilson, the transition will “drive faster decisions as we fight by realigning the cyber operations and intelligence, surveillance and reconnaissance missions under the same command.”
LEO/MEO Constellations… Pawns in Space?
Contending with the reality of future attacks, the strategy of investing in more agile, resilient satellite capabilities is being bolstered by new space.
Newly planned LEO and MEO constellations (by OneWeb, SpaceX, O3B/SES and others) are radically changing the economics, lowering the cost of satellites an order of magnitude that makes the concept of resilience through numbers and basic protection capabilities viable. As space becomes an ever more contested environment, small satellites can act as pawns on a chessboard… protecting large military and commercial satellites… the Kings, Queens, and Bishops of space.
Protecting a few critical and expensive satellites, which are obvious targets, with larger numbers of less expensive, yet agile satellites–pawns, if you will, creates a more defensible space. Or, as Joshua Hartman, Managing Partner at Renaissance Strategic Partners at a CyberSat conference in Washington DC, said, “…if I disaggregate a mission around a multi-satellite architecture … I make it harder for my adversary to take away my capability, whether it’s a kinetic or non-kinetic threat. If I have 200 satellites and they manage to take out two satellites, I still have 198 satellites available — and so the impact is minimized on a per satellite basis, which correlates to overall mission capability.”

Figure 2. Withour proper cyber security measures,
ground stations are suceptible to cyber attacks.
…And on the Ground
Cyber-attacks against vulnerable ground systems could result in the ability to access and potentially compromise sensitive satellite data and/or payloads.
A report from the Secure World Foundation identifies three primary access points for targeting a satellite: the supply chain, the land-based infrastructure that interacts with the satellite and the actual satellite while on orbit. Of the three access points, the supply chain and land-based infrastructure are ideal targets of opportunity for attackers because they are the most accessible.
In a recently published interview, KPN Chief Information Security Officer (CISO) Jaya Baloo said that, with respect to cyber vulnerability, she would focus on the ground station to determine how one could spoof or clone the communications over a poorly authenticated or an un-authenticated channel. The hacker would assume that on the un-authenticated channel, there would be one or two bands you could communicate with from your ground station to the satellite. If it was un-authenticated, the hacker could then pirate your signal communications to that satellite, she explained.
Approaches to Cyber Security
For terrestrial and space environments Kratos offers a range of cybersecurity testing, monitoring and hardening solutions to reduce vulnerability and minimize risk:
Interference Cancellation
Deliberate jamming, or RFI, is one of the more prevalent attacks. Traditional approaches to resolving interference require identifying the source and when possible working with the interfering party to mitigate the effects.
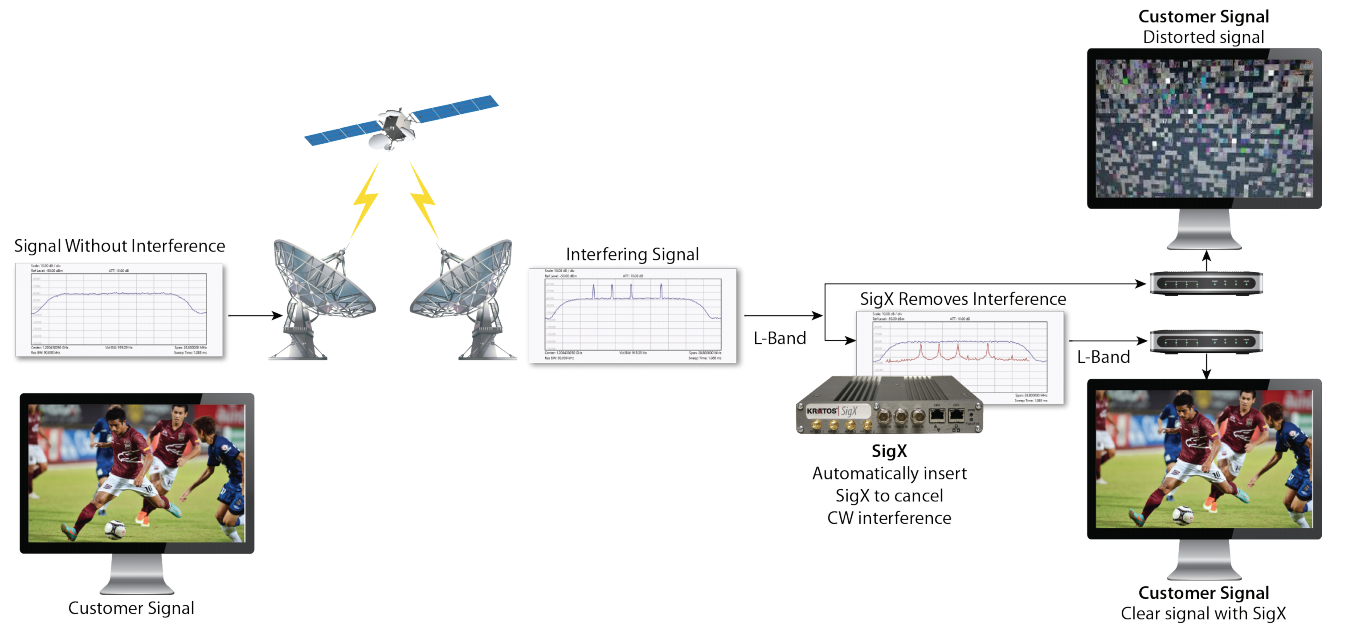 Figure 3. SigX cancels Continuous Waveform interference signals in real-time to protect valuable bandwidth.
Figure 3. SigX cancels Continuous Waveform interference signals in real-time to protect valuable bandwidth.
Monics SigX® is a proactive signal cancellation solution from Kratos that offers an alternate approach to resolving interference without relying on cooperation from the interfering party.
SigX directly mitigates RF interference (RFI) as shown in Figure 3 by simultaneously canceling up to four continuous wave (CW) or sweeping CW signals in real-time to protect valuable bandwidth and help assure application and/or mission effectiveness.
RF monitoring data has long been used to manage signal interference issues; however, RF monitoring can advance Space Situational Awareness (SSA) with its ability to identify the behavior and performance of the satellites themselves. By leveraging RF data — the information about satellite signals— SSA can better detect, characterize, and attribute threatening space activities.
With space evolving to a warfighting realm, RF data can effectively fill the gaps in traditional SSA sensors to provide more timely, thorough, and predictive awareness.
With the correct RF analytics, machine learning, and AI tools, personnel can characterize the attributes of satellites, predict the maneuvers or actions they may undertake, and discern intentions.
For example, the automated classification of bandwidth use, transmission type, and timing can help identify satellite modems, payload activities, and attribute behavior.
Figure 4. Traditional versus RF Space Situational Awareness (SSA).
Coupled with its global sensor network, consisting of 21 worldwide RF monitoring sites, hosting more than 80 fixed and steerable sensors and antennas in C-, Ku-, X-, Ka-, L- and S-bands, Kratos’ advanced analytics and AI tools process RF data for real-time SSA awareness, predictive insights, historical trending, and patterns of life. Fused and correlated with data from optical, radar, terrestrial and space-based sensors, this provides more timely, accurate, and complete SSA.
Information Assurance
Information Assurance (IA) hardening is another approach to protecting operating systems to ensure system software, firmware and applications are updated to stay ahead of exploits that attack flaws in the underlying code.
Kratos has a proven history of executing IA hardening for commercial and government organizations. The company now offers IA hardening as a service that provides consistent IA hardened operating system (OS) updates on a quarterly basis and is fully compliant with the U.S. Defense Information Systems Agency (DISA) Security Technical Implementation Guide (STIG) hardening requirements.
Security Assessments
Satellite operators use traditional security monitoring tools as well as those uniquely designed for satellites.
Kratos offers a SATCOM Cybersecurity Assessment service that addresses the increasing threats and unique requirements of the satellite industry. Cybersecurity Assessments assist satellite organizations in the identification and prioritization of threats and their mitigation.
The result is a detailed view of satellite network preparedness in addition to recommended steps required to mitigate risks and ensure compliance with applicable regulations, standards and guidelines.
CyberC4 is an integrated family of products designed for the unique cyber defense needs of satellite ground network environments including situational awareness, and active defense for total protection from cyber-attacks.
Kratos protected communications products and services continuously monitor SATCOM networks for cyber threats, harden SATCOM equipment against exploits and defend against insider threats.
The Market
The global military cyber security market is expected to have been nearly $10 billion in 2017 and is expected to increase to almost $14 billion by 2027 — that represents a CAGR of approximately 3.5 percent during the forecast period.
According to the “Global Military Cyber Security Market 2017-2027” report, the global market for military cyber security is expected to be valued at more than $130 billion during the forecast period and is expected to be dominated by North America, followed by Asia-Pacific and the European markets.
Conclusion
The cyber threat to satellites is not a U.S., European or Asian threat… these attacks are of global concern.
While anti-cyber technologies and strategies that can anticipate threats as well as react to them will be key to neutralizing cyber-attacks, they will be far more effective if nations work together, share information, develop industry-led standards for knowledge exchange, risk assessment and management, and share technology advances in a timely manner.
Just as industrial stove-piped structures can cripple innovation, so, to, can a stove-piped national approach to cyber security defeat these insidious threats.
www.kratoscomms.com


