U.S. Department of Defense (DoD) tactical/expeditionary networking and command post programs have a widely acknowledged the critical need to improve mobility. The current state of the art for tent-based command posts requires hours or days of setup, which includes thousands of feet of copper wiring that delays network availability.

To enable mobility for warfighting, the National Security Agency (NSA) established a program (with a set of guidelines) called “Commercial Solutions for Classified” (CSfC). CSfC-based mobility solutions are currently being fielded by the U.S. Marine Corps and by U.S. Army programs of record to provide command post mobility and soldier dismounted situational awareness, including using ground vehicles as network nodes and mobile command posts. However, the extensive requirements and processes involved are complex and not well understood.
This article compares various CSfC network architectures and proposes several approaches for CSfC solutions optimized for mobility use cases.
CSfC enables access to classified information using inexpensive, commercial technologies. This enables entirely new classes of wireless access to classified networks for warfighting and lets U.S. coalition partners access classified information without taking possession of controlled cryptographic items (CCI). The use of CSfC significantly reduces equipment costs and simplifies key management, equipment handling and security procedures.
CSfC guidelines provide configuration options that allow classified data to be transmitted using two layers of Commercial-Off-The-Shelf (COTS) encryption products. Previously, the only way to transmit classified data was by using expensive, controlled, military grade encryption devices, such as TACLANEs (Tactical FASTLANE, or, Tactical Local Area Network Encryption and protects networks against threats as well as defends assets across all domains) and KG- 250s (Type 1 network encryptor).
CSfC mobility and wireless solutions provide enormous potential to enable command post mobility and soldier- dismounted situational awareness, including the use of ground vehicles as radio nodes. Research and design for such use cases are currently underway. In order to satisfy CSfC and DoD guidelines for classified networking, systems integrators and technology developers must meet an extensive set of requirements and processes that are both complex and not well-understood.
This article describes, compares, and contrasts various CSfC network architectures and proposes several approaches for CSfC solutions optimized for tactical networks and mobility use cases.
CSfC Architecture + Process
Using CSfC, classified information can be transmitted over untrusted wireless networks such as Wi-Fi, LTE, and SATCOM, including public, government, and partner networks. This is achieved by using two sets of encryption technologies, one layered inside the other.
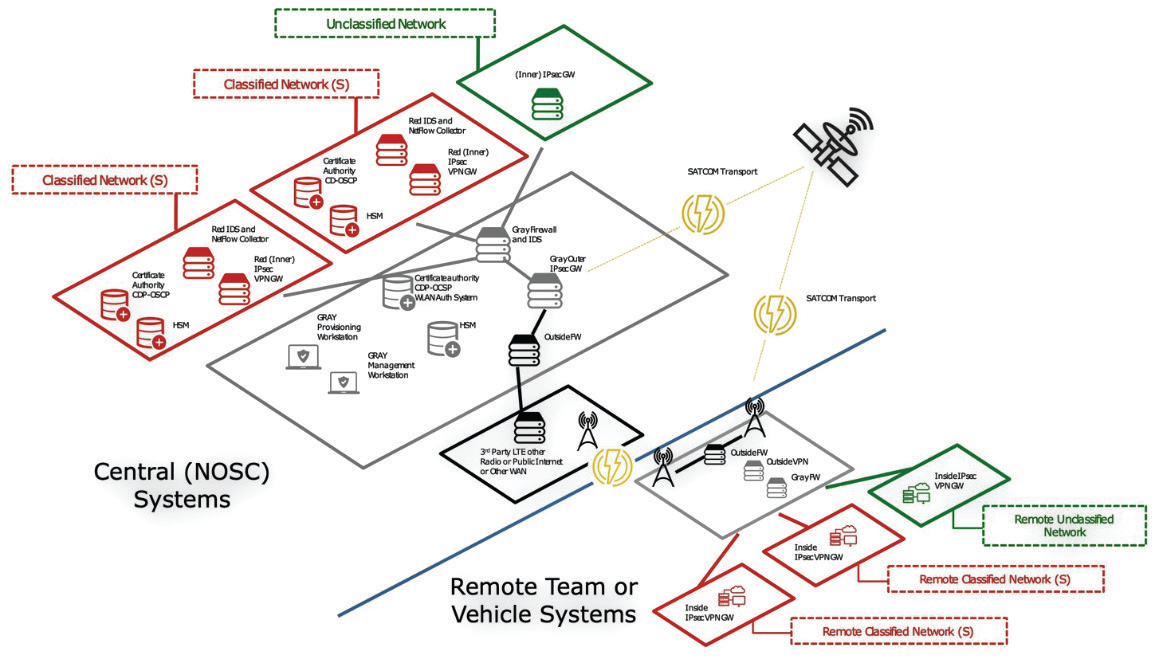 Figure 1. WAN encryption using dual VPN MSC CP.
Figure 1. WAN encryption using dual VPN MSC CP. 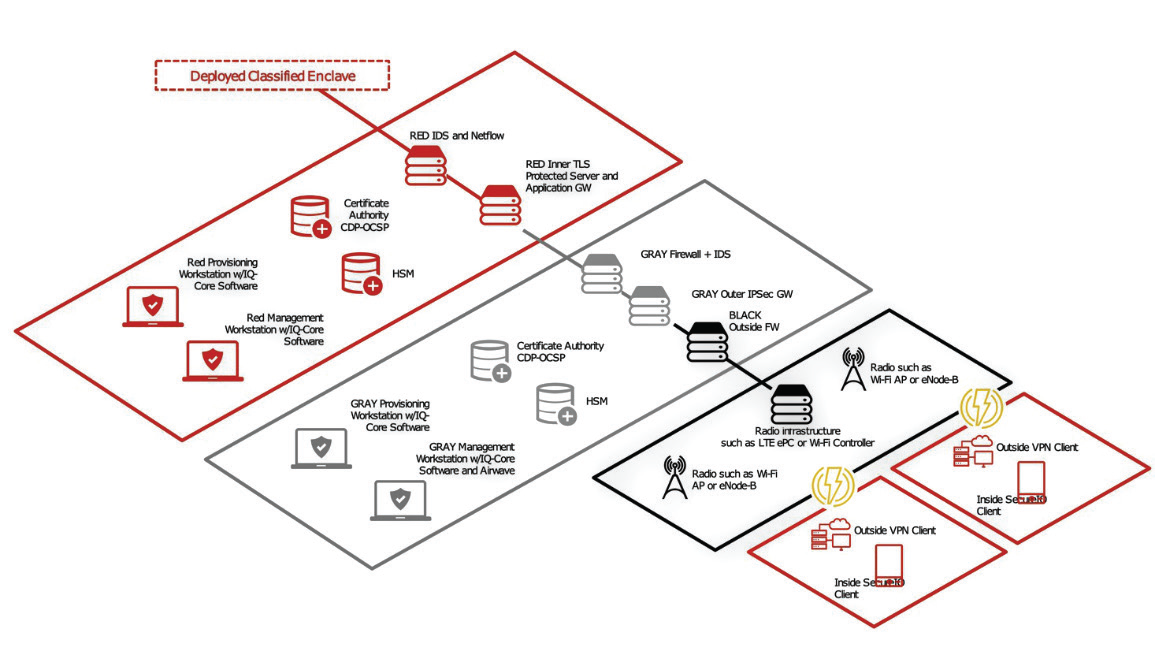 Figure 2. WLAN encryption using Wi-Fi WLAN CP.
Figure 2. WLAN encryption using Wi-Fi WLAN CP.
Approved configurations include encryption using VPN inside VPN, VPN inside Wi-Fi WPA2, MACsec inside VPN, and TLS inside VPN. Though layered encryption is straightforward in concept, full CSfC implementations must include a breadth of technologies, including public key infrastructure (PKI), encryption gateways and clients, authentication systems, cybersecurity technologies, and secure network infrastructure. Additionally, to successfully field systems, the CSfC program requires organizations to follow a well-defined process.
CSfC Program Overview
Organizations can select from the following CSfC-related technology and process components to create integrated solutions that enable classified networking over radio infrastructure such as SATCOM, Wi-Fi, LTE, or LMR, enabling vehicles to communicate with upper echelons/HQ, or enabling soldiers to use mobile devices such as laptops, tablets or smartphones, in transit, at-the-halt, and in dismounted use cases.
• Cryptographic Primitives: the approved algorithms and mathematics that the CSfC specifies for transmission of classified information
• Encryption Protocols: are approved to conduct communications between devices that transmit encrypted data. Most used today are VPN solutions providing data-in-transit encryption DAR (Data-at-Rest): encryption technology used to encrypt data stored on media such as hard drives, flash drives, etc.
• Public Key Infrastructure (PKI): the approved technologies and protocols required to manage trust, encryption key generation, and sharing
• Key Validation and Testing Processes: required by the CSfC program in order to comply with CSfC rules
• Detailed CSfC Architectures (Capabilities Packages)
There are several main CSfC architectures for transmitting classified information over Wide Area Networks (WAN) and Wireless Local Area Network (WLAN) infrastructure, depending on the desired use cases. These architectures are specified in “Capability Packages” that outline — in great detail — the components, configurations, processes, and testing required by the government before they will approve the use of a system. The following architectures are most suited for use in tactical/expeditionary use cases, for both WAN communications with upper echelons/HQ or teleport sites, and WLAN communications for shortrange communications with end-user devices.
A. Multi-Site Connectivity Capability Package
This configuration provides the ability to use any type of wireless transport for network WAN access, including SATCOM, Wi-Fi, LTE, or other radio types, so that deployed, remote CSfC gateways may include a minimum of deployed equipment. This architecture depicts the Multi-Site Connectivity Package Access Capability Package[1], with a Central Management Site (NOSC) and a remotelymanaged site using two layers of IPsec VPN encryption.
This architecture also allows for multiple network classifications sharing a gray network and transport infrastructure. In the case of ground vehicles, the remote system could be vehicle-mounted. Depending on the number and type of networks being accessed, as well as bandwidth requirements, the remote system could comprise just two small vehicle-mounted or soldiercarried VPN gateways.
B. Campus WLAN Capability Package
For organizations looking to develop fly-away or vehicle-mounted classified WLAN systems that can enable at-the-halt or on-the-move and dismounted situational awareness (SA) over short distances, the Campus WLAN Capability Package[2] architecture is an option. The architecture above assumes a pre-existing WAN encryption solution and adds the deployment of Wi-Fi so that end-user devices (EUDs) can be used on a wireless LAN with access to classified information.
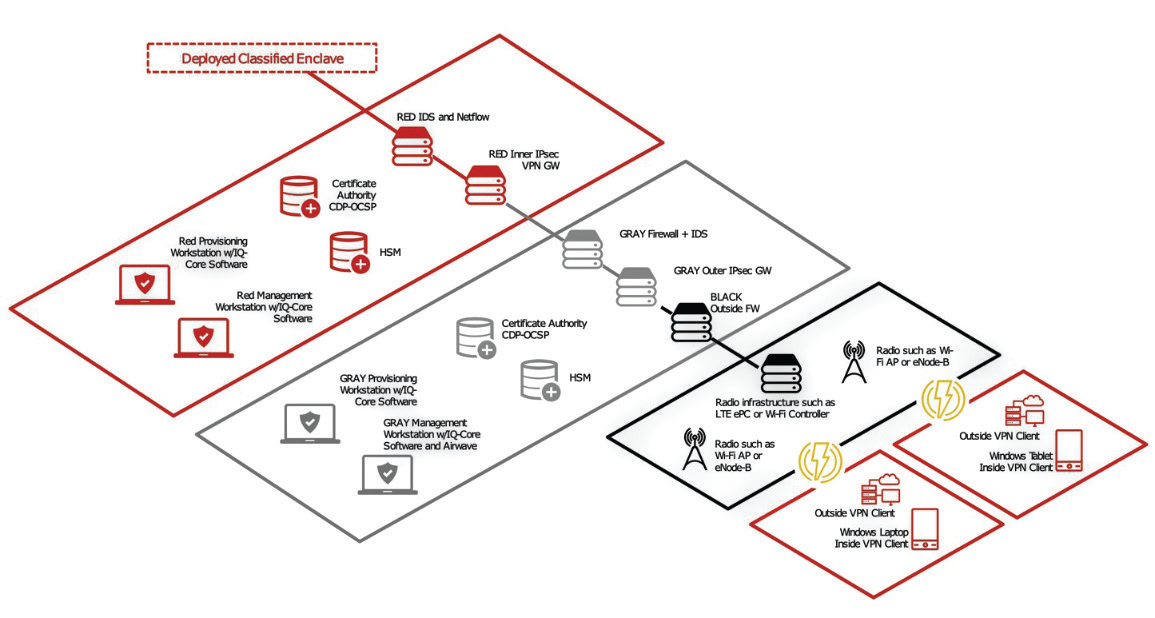 Figure 3. WLAN encryption using any radio via MA CP VPN EUD.
Figure 3. WLAN encryption using any radio via MA CP VPN EUD. 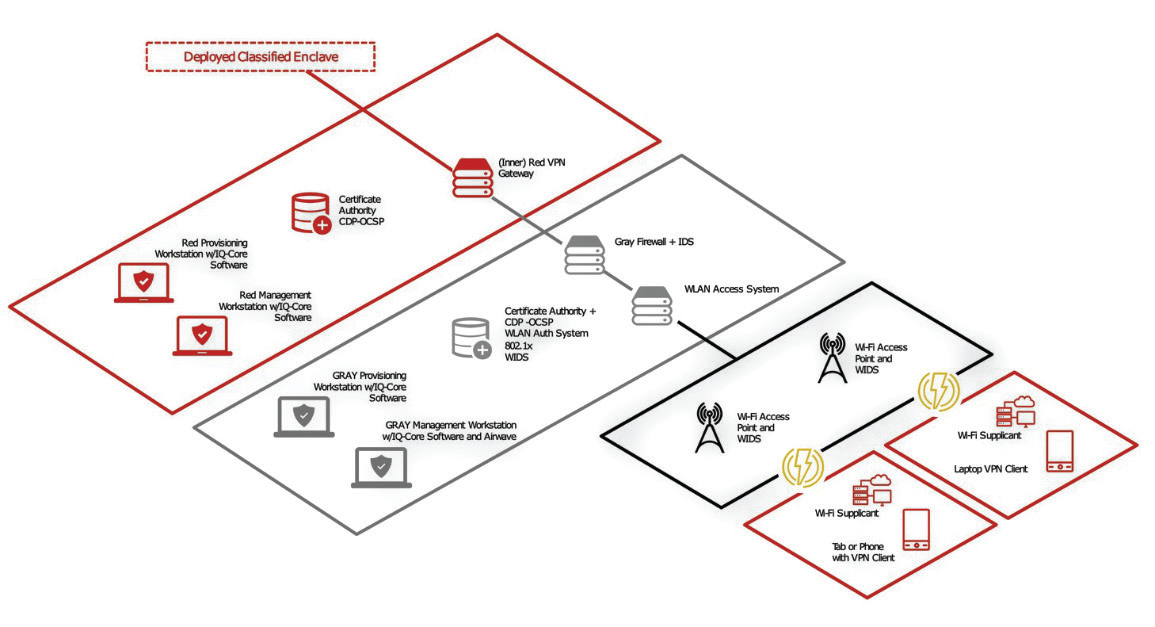 Figure 4. WLAN Encryption Using Any Radio via MA CP TLS.
Figure 4. WLAN Encryption Using Any Radio via MA CP TLS.
This architecture uses the Campus WLAN Capability Package, using built-in, commercial, Wi-Fi stack (supplicant) and OS security on the EUD to provide one layer of the required two-layer package. The architecture uses a single IPsec VPN client on the EUD to provide the second, inner encryption layer. This architecture provides for a straightforward EUD configuration using well-tested approaches.
C. Mobile Access Capability Package with VPN EUD
Technology Selection + Deployment Considerations
While CSfC solutions can transform communications for the soldier by enabling classified networking over wireless infrastructure, they have two significant issues: size and complexity. The CSfC program requires that solutions include comprehensive suites of security technologies at the command post or datacenter, and that the technologies be provided by different vendors. With the number of required components in CSfC systems, vehicle integration can be a challenge due to the size, weight, and power (SWaP) limitations imposed by vehicles. The diversity of equipment also creates a system configuration, management, and training burden that many organizations are under-equipped to manage. The following sections address methods to mitigate these challenges.
Size, Weight, and Power
For example, new tactical equipment, as compared to legacy 19” rack mount equipment, on average:

Figure 6. Rugged PacStar communications equipment mounted on a
U.S. Marine Corps. JLTV
+ Is 10.4 times lighter than a typical 1ru server
+ Is 12.4 times smaller than a typical 1ru server
+ Consumes up to 18 times less power These types of low SWaP solutions enable maximum program flexibility, enabling vehicle-mounted, roll-on/roll- off, fly-away, and stationary use cases, all using the same hardware platform.
SWaP Savings Made Possible
To ensure reliable uptime of CSfC solutions in vehicle mount applications, components should be selected that have completed and passed MIL-STD testing appropriate for vehicle-mounted use cases, including for environment, EMI, and power (MIL-STD-810G and MIL-STD-461F). These tests should have been conducted by independent, outside laboratories, and, where applicable, with the equipment powered on and operating.
Some manufacturers may cut corners on tests, test to a subset of these standards, or simply claim products are “designed for MIL-STD 810,” leaving considerable schedule and project cost risk, since a complete set of independently validated test reports will be required before fielding solutions by government agencies. Organizations should consider solutions that have undergone at least:
+ (18) types of MIL-STD-810G/H environmental tests, including vibration in a variety of vehicles (ground, helicopter, etc.), shock, crash safety, high/ low temperature, humidity, altitude, acceleration, blowing sand/dust, and explosive atmosphere – at the component and chassis level.
+ (7) types of MIL-STD-461F/G EMI tests, including radiated emissions, radiated susceptibility, conducted emissions, conducted susceptibility — at the entire solution level.
Packaging
The government continues to evolve CSfC guidelines, frequently adding requirements as threats evolve and technology improves. Organizations looking to deploy CSfC solutions should consider modular systems that are flexible and easily upgradeable, avoiding costly fork-lift replacements, supply chain, and logistical rework.
 IQ-Core Crypto Manager
IQ-Core Crypto Manager
Currently, there are options available that address these needs through modular design, including vehicular rack mount solutions. Some solutions include the ability to replace modules without requiring tools. Some systems include completely dismountable solutions with a built-in UPS.
Configuration Management and Monitoring
To address the added complexity and training burden imposed by the two layers of encryption and extensive security requirements, organizations should consider CSfC-focused configuration management tools, such as PacStar IQ-Core Crypto Manager. IQ-Core Crypto Manager simplifies the setup, configuration, and management of the underlying equipment and devices used in CSfC solutions.
IQ-Core Crypto Manager can provide a base level of capabilities, including:
+ Simplifying the deployment of CSfC solutions, with attendant benefits, while reducing the amount of added complexity and training
+ Providing a unified interface (“a single pane of glass”) to underlying equipment from multiple vendors
+ Providing a means to monitor multiple sets of equipment, in fixed/branch offices and tactical settings, enabling lightly trained operators to manage the equipment
Organizations should consider functionality specifically designed to make CSfC manageable, including:
VPN Setup Wizards
VPN setup and certificate generation wizards reduce the complexity of providing the correct information to the devices involved in CSfC encryption by providing step-by-step wizards, insulating lightlytrained users from dealing with the command line interfaces and multiple UIs across the underlying devices.
VPN Monitoring/Troubleshooting
VPN monitoring capabilities include the ability to display, in real time, the connection and configuration status of one or more VPN devices. Status indicators should include status of the active authentication and bulk encryption settings in use, ensuring the connection follows CSfC guidelines.
Certificate Management
Management capabilities include automating the process of managing device certificates, a process that is error-prone, and requires extensive training. Reducing the opportunity for errors in this process helps ensure uptime and allows security administrators to focus on more important tasks. Capabilities related to certificates should include:
+ Generation of certificate signing requests
+ Display of certificate details and expiration dates, including expiration alerts
+ Encrypted transmission of certificate signing requests
+ Management of the signing process at either the deployed systems or at the NOSC
+ Management/monitoring of certificate authorities
+ Certificate revocation checking via built-in OCSP and CDP functions
By using IQ-Core Crypto Manager as described, the U.S. Army is deploying CSfC solutions and gaining the benefits of Wi-Fi in tactical settings, reducing command post setup time and enabling new classes of wireless applications, while limiting management complexity and training burdens.

Dominic Perez, CISSP is the CTO at Curtiss-Wright Defense Solutions and a Curtiss-Wright Technical Fellow, with PacStar since 2008 he joined Curtiss-Wright through their acquisition of PacStar in 2020. In the past 13 years, he has supported development of PacStar’s rugged, tactical hardware and IQ-Core Software serving as the subject matter expert for compute, virtualization and virtualized network functions. Dominic is part of the team that won tactical networking equipment and software awards for numerous DoD tactical programs including the US Army T2C2, US Army SFAB, US Army ESB-E, PM TN Secure Wireless Small Form Factor, PEOC3T TCNO, and US Marine Corps NOTM vehicle-mount and deployable communications programs.
Dominic currently leads the teams developing Curtiss-Wright’s PacStar Commercial Solutions for Classified, Modular Data Center, and Tactical Fusion System product lines deploying cutting edge secure communications, edge data processing, and rapid sensor to shooter situational awareness to the warfighter at the tactical edge systems in the face of disconnected, limited, and intermittent (DIL) comms environments.

Prior to PacStar, Dominic worked for Biamp where he created automated testing infrastructure for the hardware, firmware and software powering their network distributed audio, teleconferencing and paging systems. Dominic studied mechanical engineering and computer science at Oregon State University. He currently holds multiple professional certifications from VMware in Data Center Administration; Cisco in Design, Security, and Routing/Switching; and EC Council and ISC2 in Security.
www.curtisswrightds.com/


